Stop Compromising Developer Security with Phone Numbers - Website
Por um escritor misterioso
Last updated 11 novembro 2024


Cisco Secure Endpoint (Formerly AMP for Endpoints) - Cisco

How to Prevent SQL Injection: Attacks and Defense Techniques

The mechanics of a sophisticated phishing scam and how we stopped it

Examples of Code Injection and How To Prevent It
.jpg)
How to Protect Your Phone Against a SIM Swap Attack

1 in Cloud Security & Endpoint Cybersecurity

Identity Theft Resource Center's 2022 Annual Data Breach Report

From cookie theft to BEC: Attackers use AiTM phishing sites as

Identity Theft Resource Center's 2021 Annual Data Breach Report
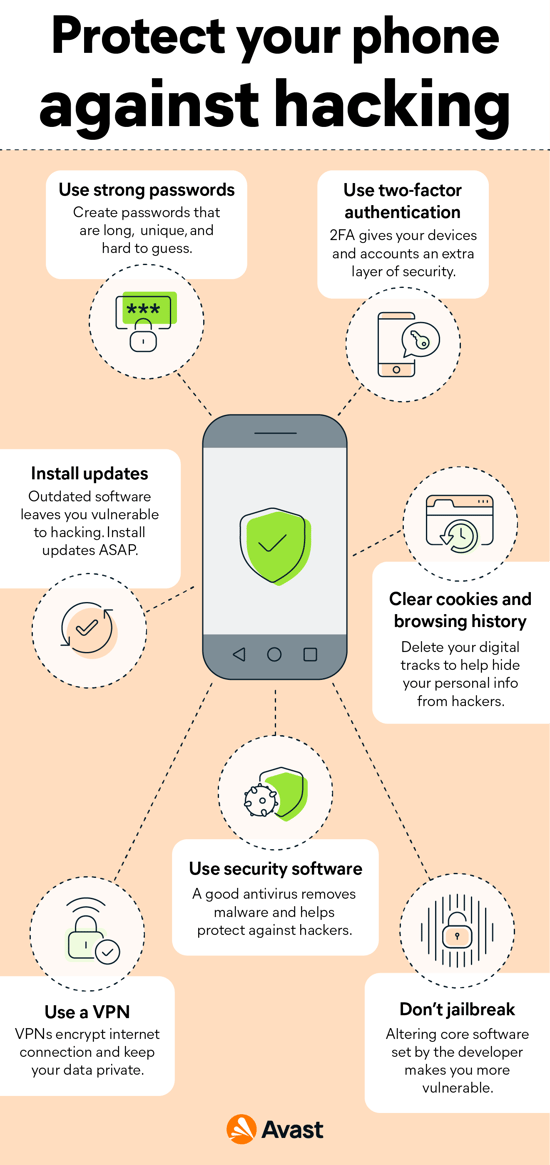
10 Signs That Your Phone Has Been Hacked

Top 10 Web Hosting Security Best Practices

Session Replay, Product Analytics, Error Tracking

What to Do If You've Been Hacked
Recomendado para você
você pode gostar
:max_bytes(150000):strip_icc()/Roblox_Lineup_2020small-28e606de166b4089b337eb0c291f9d1f.png)










![Apple Watch SE (2nd Gen) [GPS 44mm] Smart Watch w/Starlight Aluminum Case & Starlight Sport Band - M/L. Fitness & Sleep Tracker, Crash Detection, Heart Rate Monitor, Retina Display, Water Resistant](https://m.media-amazon.com/images/W/MEDIAX_792452-T2/images/I/A1dYhdrpe7L._CR3,0,1914,1080_SR684,386_.jpg)
/i.s3.glbimg.com/v1/AUTH_e7c91519bbbb4fadb4e509085746275d/internal_photos/bs/2023/K/Z/tRbwwYQyuolIfTcua45g/the-rock-dwayne-johnson.jpg)





