Cmd Hijack - a command/argument confusion with path traversal in cmd.exe
Por um escritor misterioso
Last updated 11 novembro 2024

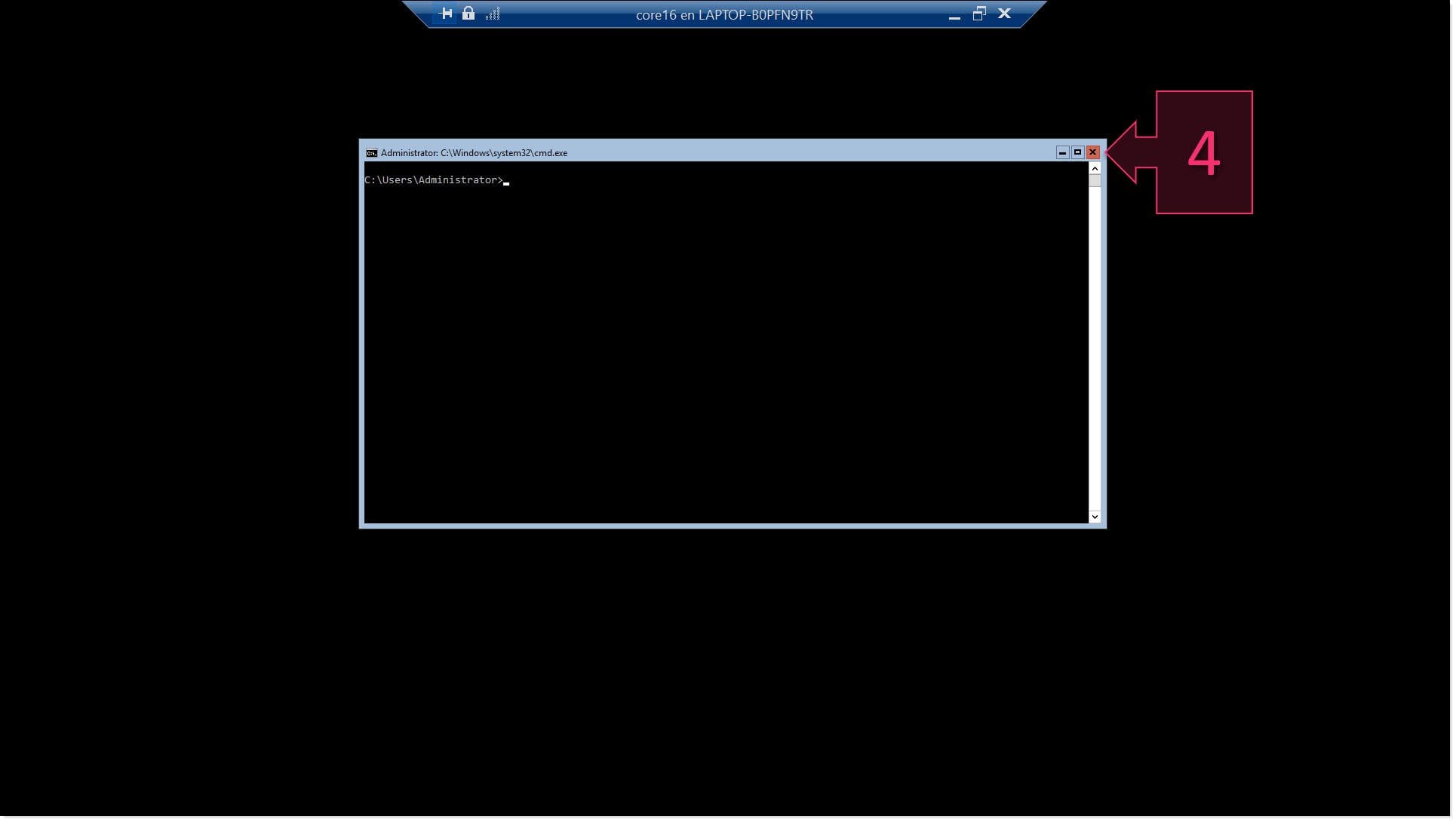
This one is about an interesting behavior 🤭 I identified in cmd.exe in result of many weeks of intermittent (private time, every now and then) research in pursuit of some new OS Command Injection attack vectors.
So I was mostly trying to:
* find an encoding missmatch between some command check/sanitization code and the rest of the program, allowing to smuggle the ASCII version of the existing command separators in the second byte of a wide char (for a moment I believed I had it in the StripQ
Dissecting Macro Malware - Use CMD Path Traversal Hijacking Technique (PING!) - Malware Analysis - Malware Analysis, News and Indicators

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles
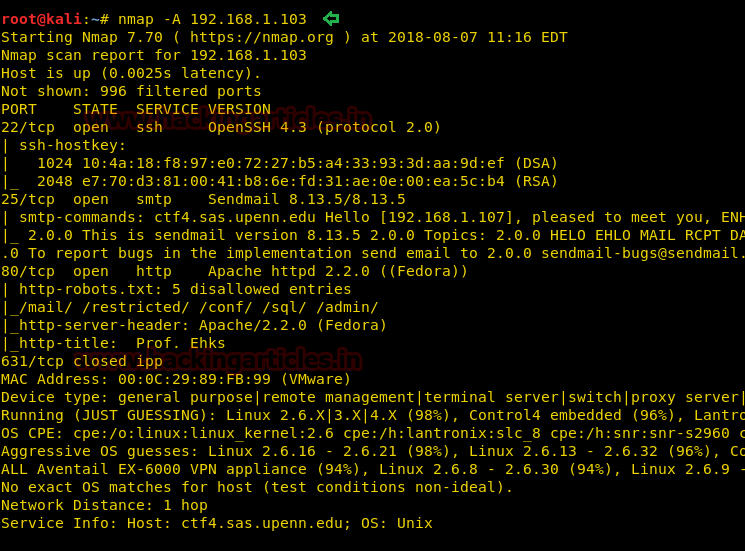
Hacking ArticlesRaj Chandel's Blog

Swedish Windows Security User Group » Microsoft security intelligence

Security Bulletin 1 Nov 2023

Cmd Hijack - a command/argument confusion with path traversal in cmd.exe

Owasp Asdr Application Security Desk Reference Soc2008 Alpha, PDF, Computer Security
How to handle CMD start with '&' in the command path with Windows 10 (windows, command line, command-line arguments, escape characters, admin) - Quora
Cmd Hijack - a command/argument confusion with path traversal in cmd.exe : r/netsec


0xdf hacks stuff CTF solutions, malware analysis, home lab development

V0lCk3r (@ourahali) / X

Machine learning from idea to reality: a PowerShell case study, NCC Group Research Blog
Recomendado para você
você pode gostar