Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 10 novembro 2024

Describing activities of a crime group attacking Ukraine.
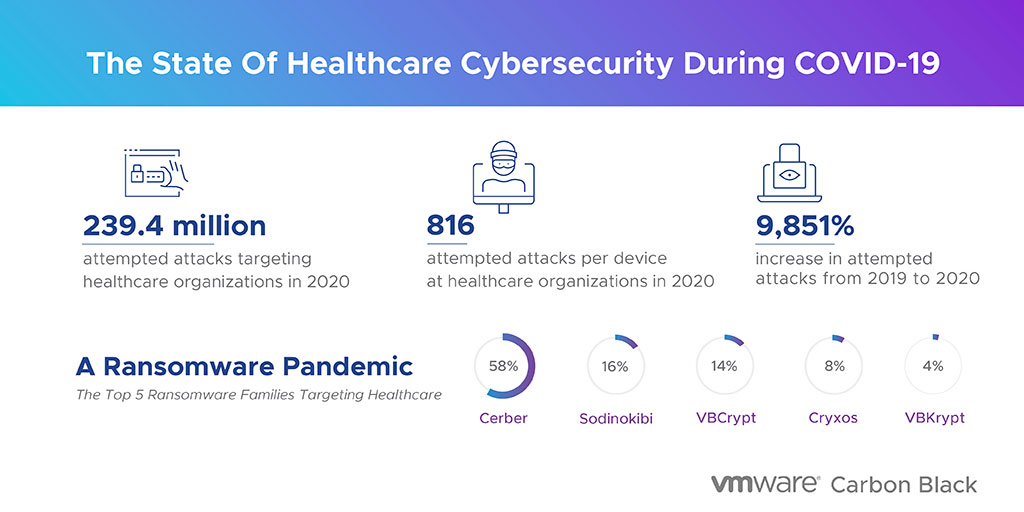
The State of Healthcare Cybersecurity: VMware Carbon Black Explores the Surge in Cyber Threats - REAL security

Security in product lifecycle of IoT devices: A survey - ScienceDirect
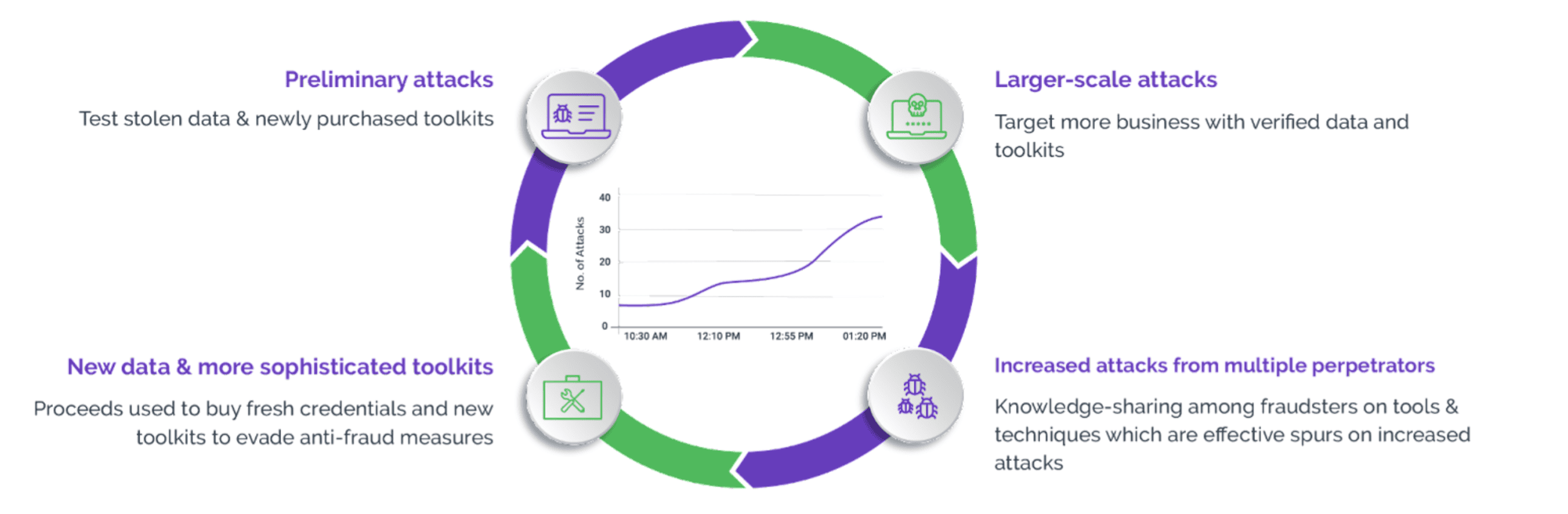
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

aa23-061a-stopransomware-royal-ransomware 0.pdf - TLP:CLEAR Product ID: AA23-061A Coauthored by: March 2 2023 #StopRansomware: Royal
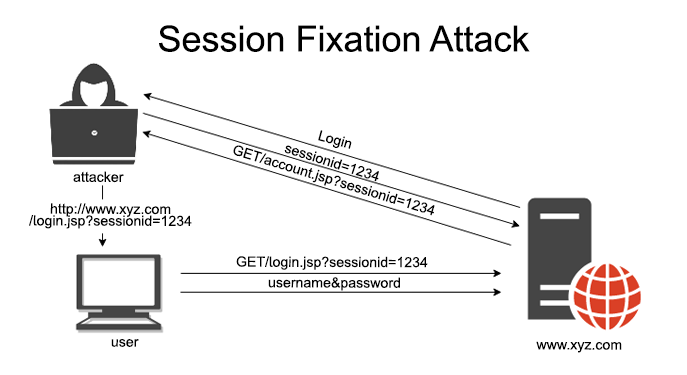
Session Side Hijacking Vulnerability in Ethical Hacking - GeeksforGeeks
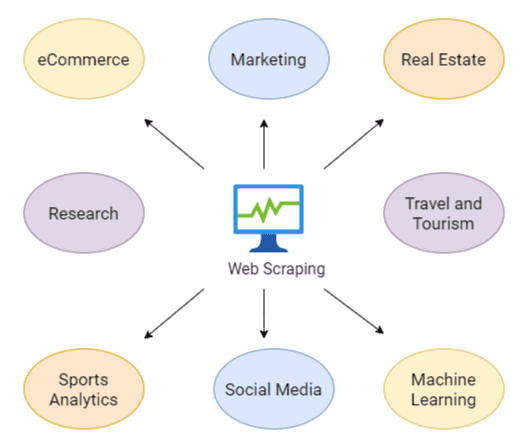
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Briefing 18 March 2022

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat
Recomendado para você
você pode gostar