a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Por um escritor misterioso
Last updated 21 setembro 2024


A new Copy-Move forgery detection method using LIOP - ScienceDirect

a1), (b1), (c1), and (d1) shows forged images having multiple
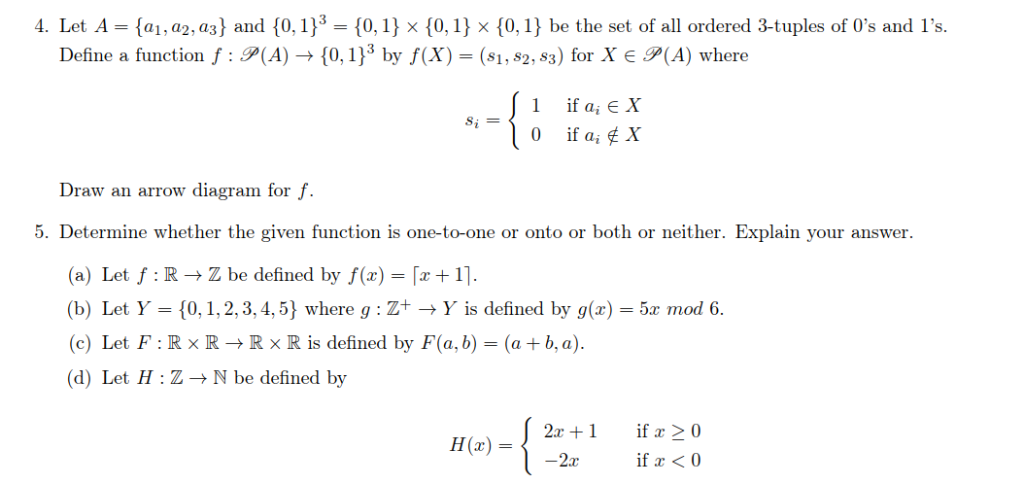
Solved 1. Let A - (a1, a2, a3) and (0, 1)3- 0,1 x 10, 1) x

SMDAF: A novel keypoint based method for copy‐move forgery detection - Yue - 2022 - IET Image Processing - Wiley Online Library
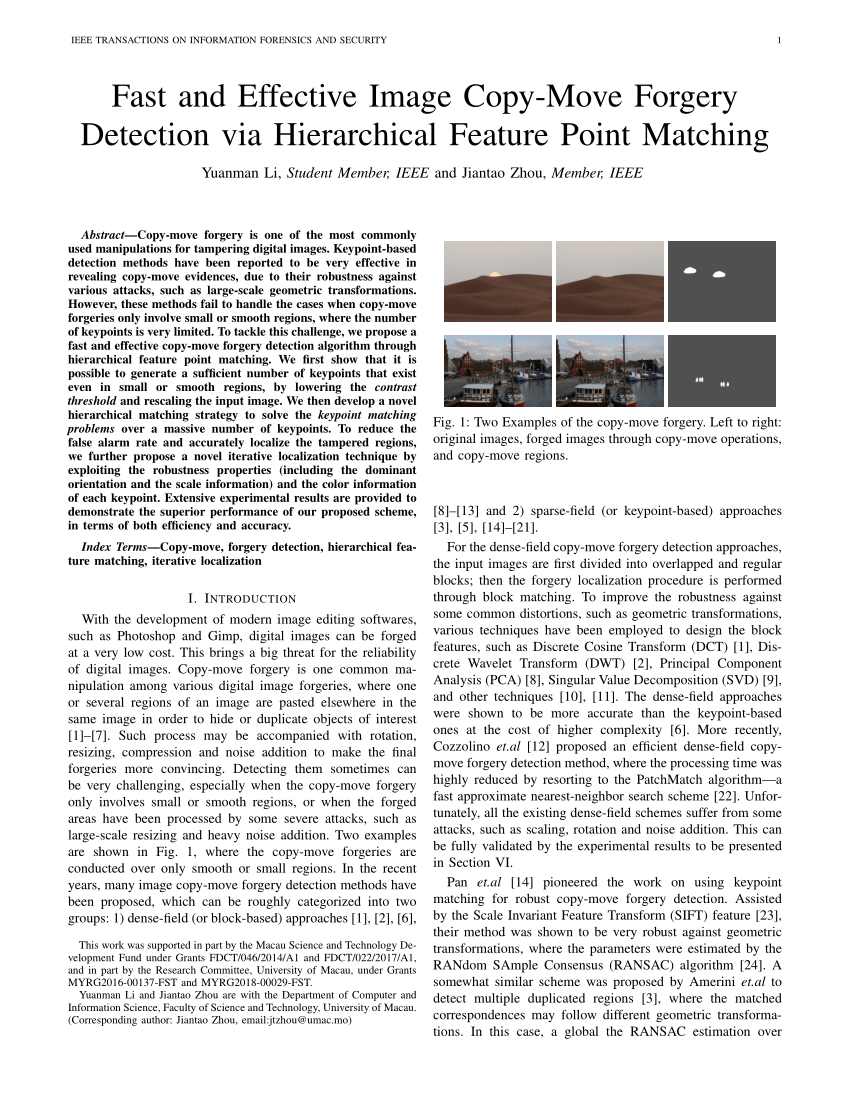
PDF) Fast and Effective Image Copy-Move Forgery Detection via Hierarchical Feature Point Matching

A New Robust Reference Image Hashing System

The first five examples for Copy-Move forgery detection: original
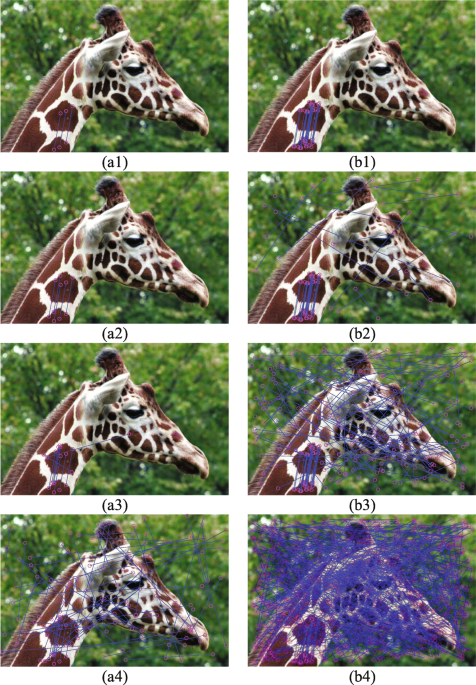
Copy-move image forgery detection based on evolving circular domains coverage
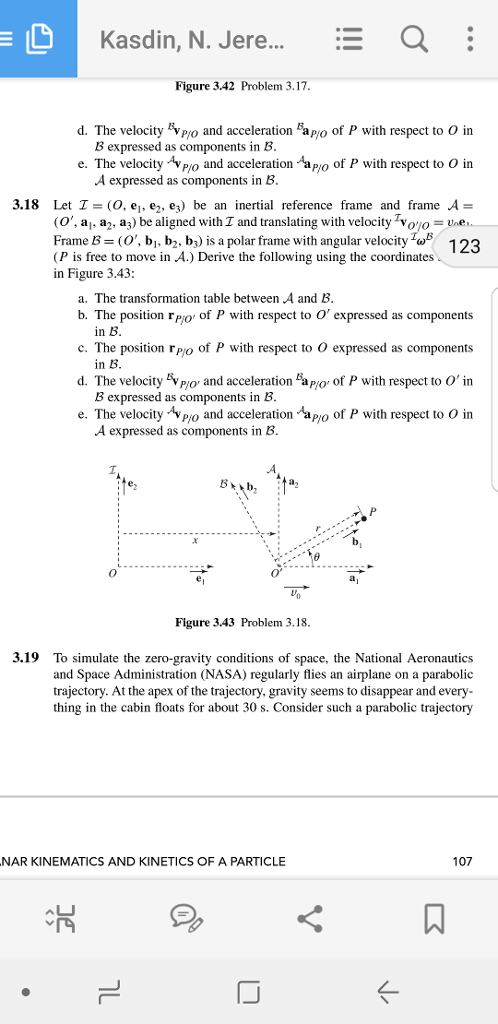
Question 3.18 Let I = (O, e1, e2, e3) be an
Recomendado para você
você pode gostar



















