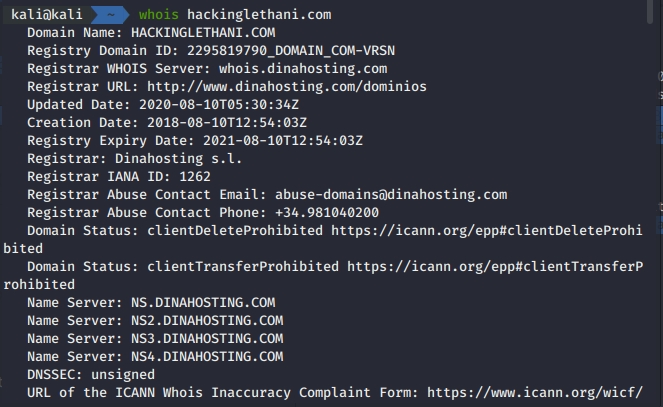
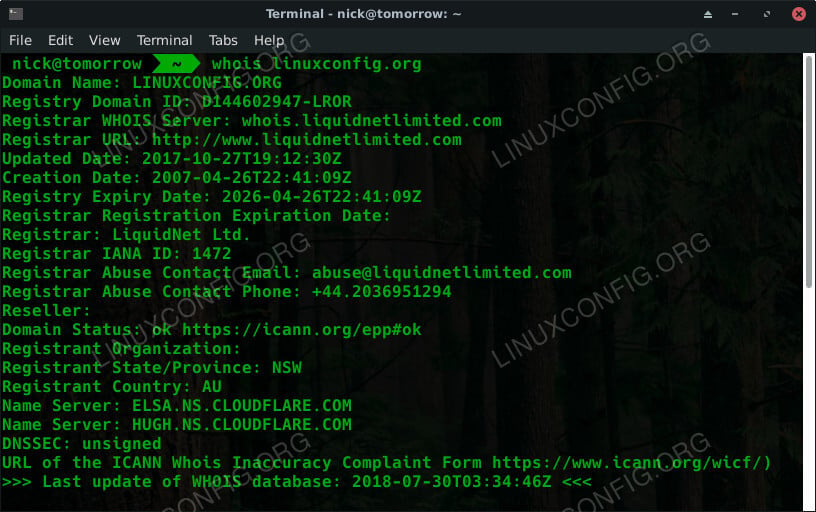
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 21 setembro 2024
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Whois Lookup Ethical Hacking

7 powerful pentesting tools (& why you should stop pedestalizing them)

Certified Information Security And Ethical Hacker
Ronin Hack: North Korea's Lazarus Behind $540 Million Axe Infinity Breach

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Russian APT hacked Iranian APT's infrastructure back in 2017

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Tips for Investigating Cybercrime Infrastructure

Hackers breached Greece's top-level domain registrar

DNC Hacks: How Spear Phishing Emails Were Used

Hezbollah's cyber unit hacked into telecoms and ISPs
Ethical Hacking - How to start

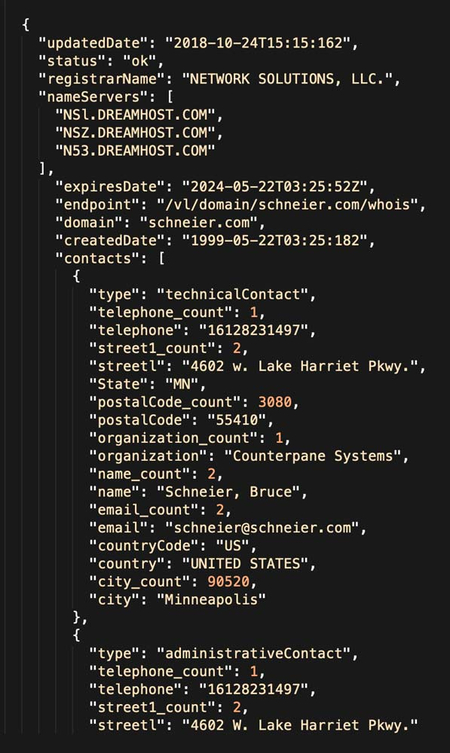
The Black Hat, the Ethical, and the WHOIS Hacker
Recomendado para você
você pode gostar










![LEGO Marvel sets for January 2023 revealed with new Hulkbuster, Quinjet, Morbius, and more [News] - The Brothers Brick](https://s3-us-west-2.amazonaws.com/media.brothers-brick.com/2022/11/LEGO-Marvel-Super-Heroes-January-2023-TBB-Cover.jpg)
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2022/k/4/QL3zgXROu8NSGIbuvCfA/loud-aspas.jpg)
/i.s3.glbimg.com/v1/AUTH_bc8228b6673f488aa253bbcb03c80ec5/internal_photos/bs/2021/U/n/6UfhHVSTiv5ZCZLSo67A/whatsapp-image-2021-10-13-at-17.29.47.jpeg)