User blog:ImASubscriberToLoganAlt/Hacker.
Por um escritor misterioso
Last updated 22 setembro 2024
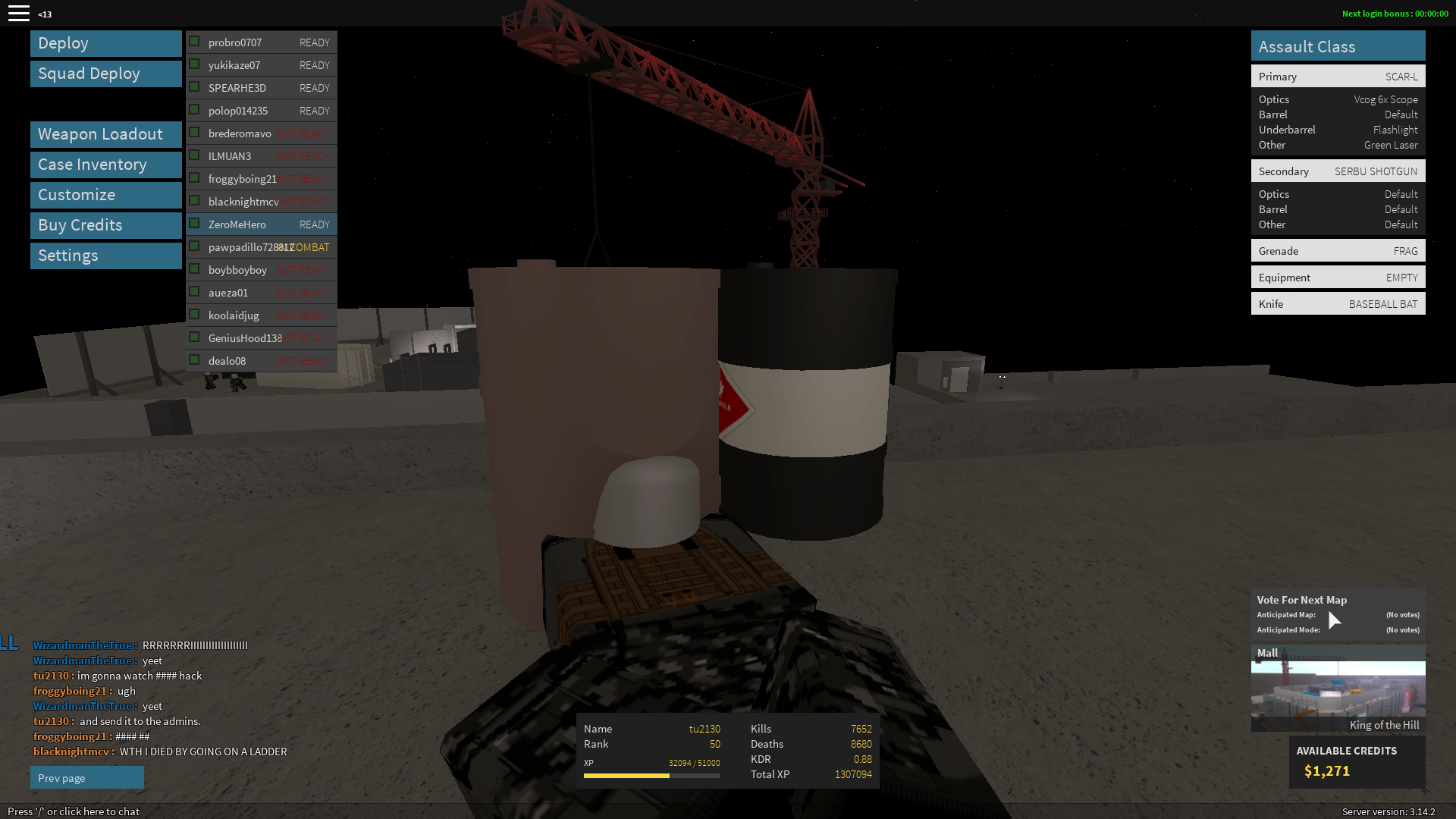
Hi, i found a hacker His name is ZeroMeHero Here's proof: Please ban this guy.

HackerOne Community Blog

Nab Hashes without Admin via Internal Monologue - Practical Exploitation [Cyber Security Education]

HackerOne Community Blog

Hack The Box Blog Cybersecurity & Hacking News

HackTheBox – SecNotes Ivan's IT learning blog

HackerSploit Blog - Videos

HackerSploit Blog - Videos

S Hacker operates by using advanced methods to obtain data from a targeted phone remotely like that…, by Benjamin Evelyn, Nov, 2023

Hack The Box Blog Cybersecurity & Hacking News
Recomendado para você
você pode gostar
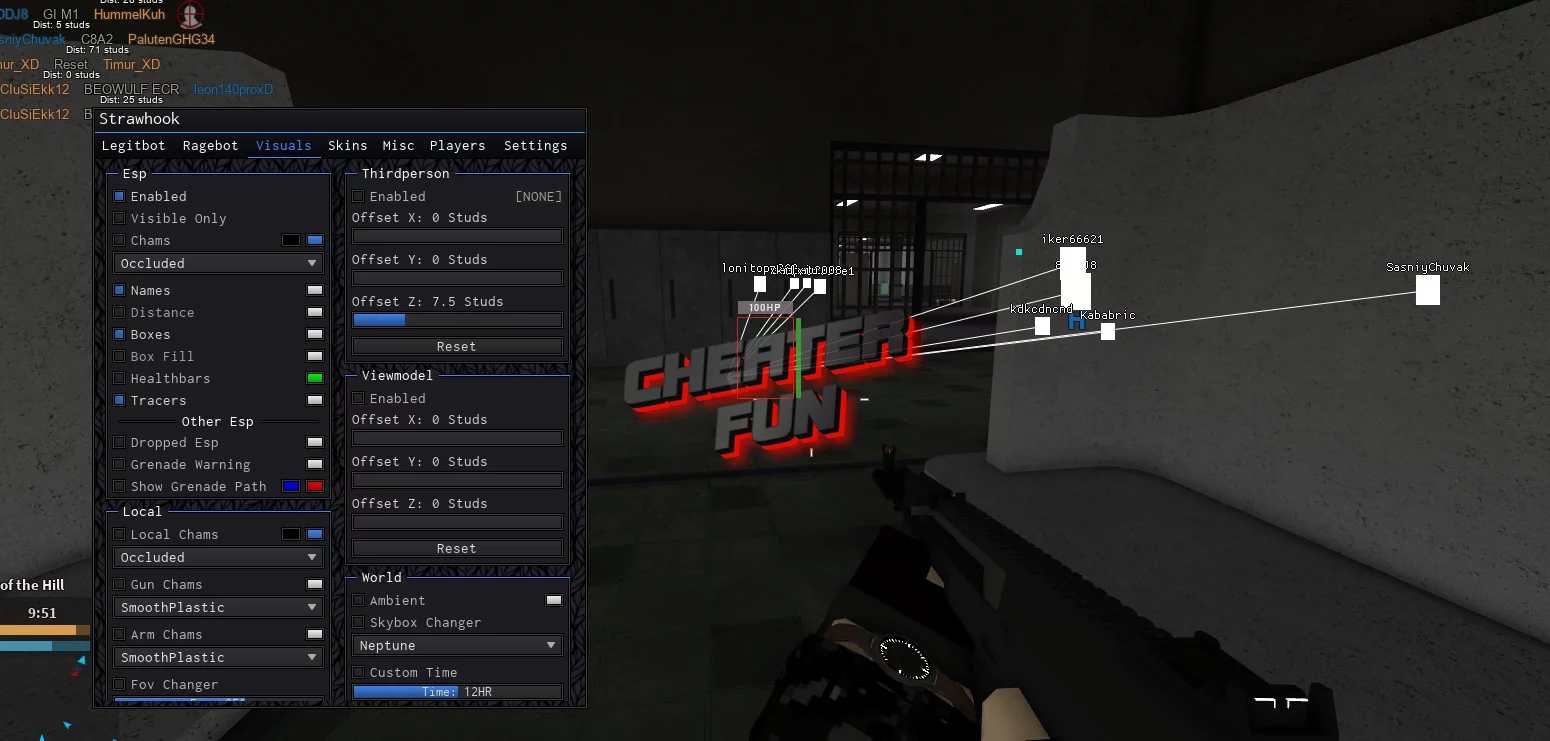

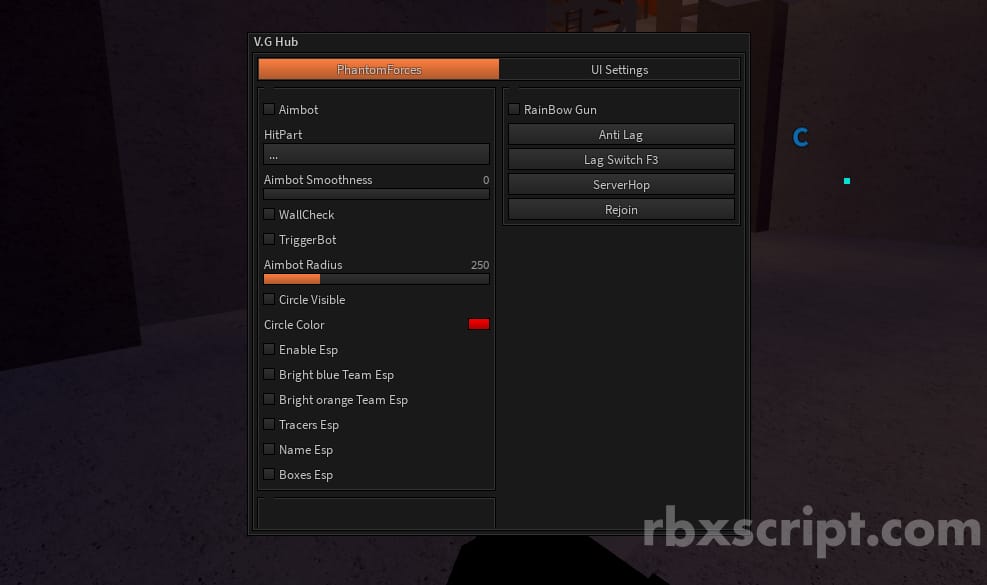
![New] Phantom Forces Script 2023](https://freerobloxscripts.com/wp-content/uploads/2023/07/image_2023-07-25_160456411-1024x576.png)
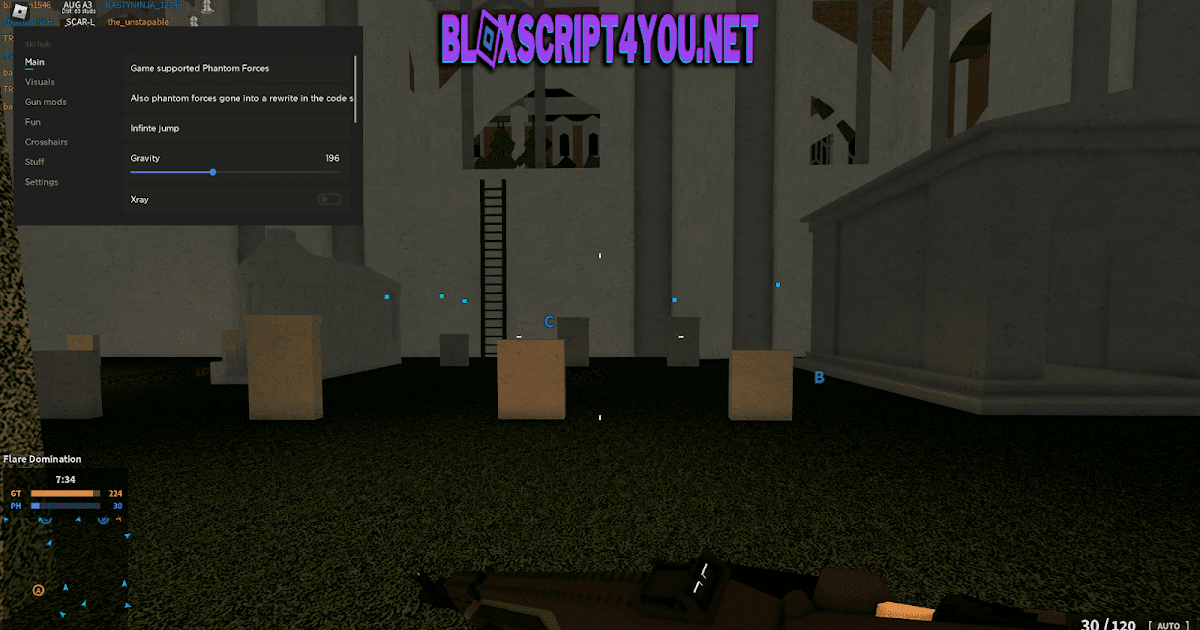

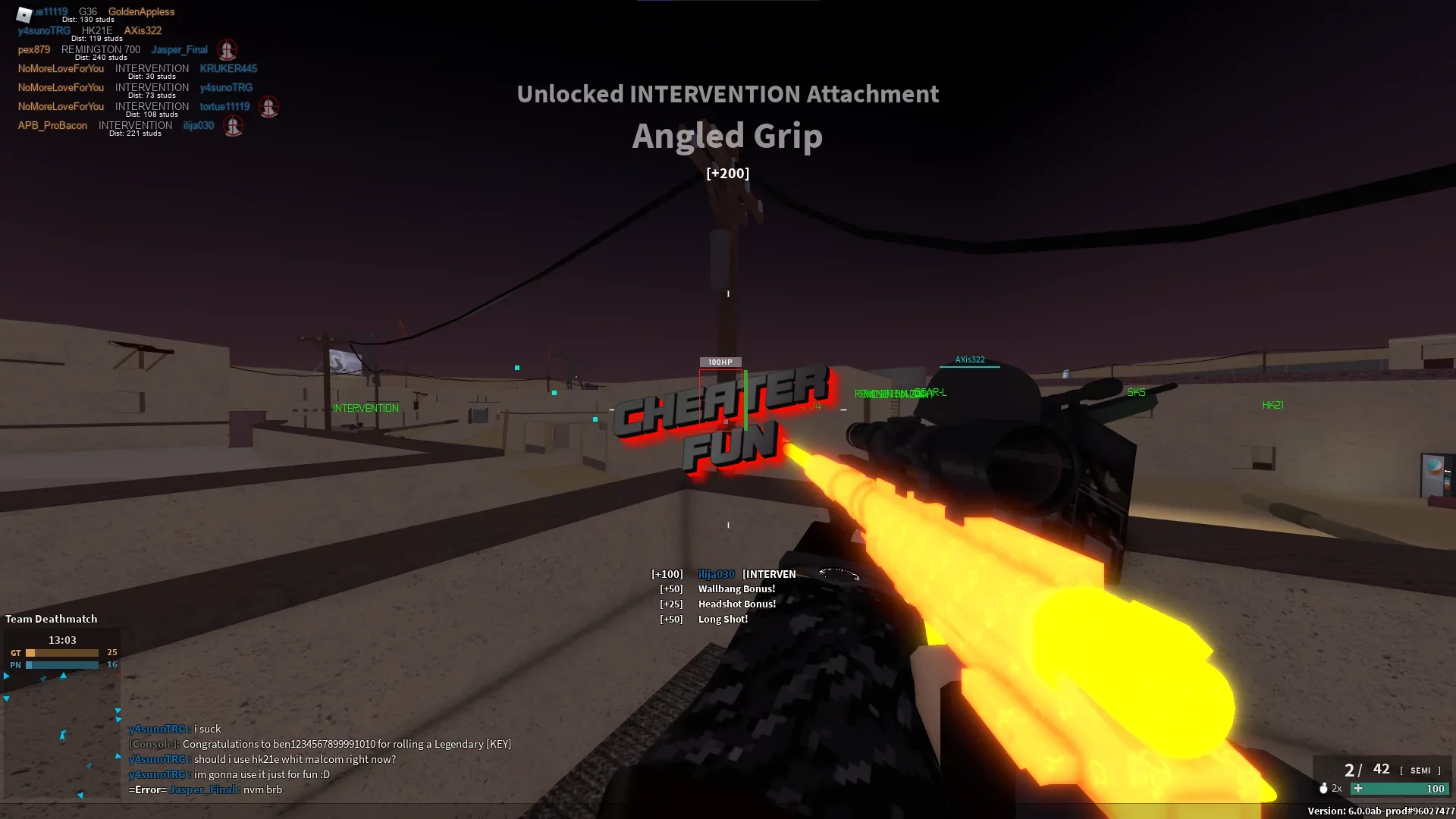
![Roblox Script - Phantom Forces [ESP]](https://blogger.googleusercontent.com/img/a/AVvXsEi7T-ggq_GGhNR2Fe4TQnjTgcdsDqRgy8bL_WBejmMcyTuAjg1sZcsjZsfgTLeZRUjghh0J-U-1Iuh1Jww6MvHjKoh8XVvuYg0mOukTR7eMOcxjiM5pdAAwcfRxzolHF1GzJlgAa7aBmItS3RUtC1pIt8I4K_xU-qVwa55UIorQH-eAgxFyYHdNaCtKew)


/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2022/n/G/T6m0QGQ7yAWhXpfVvrTA/6a79f5fec6a8a3798f835810ad09f964-4096x2730-79d759bc-1200x.webp)