Pawn Storm Abuses OAuth In Social Engineering Attacks
Por um escritor misterioso
Last updated 11 novembro 2024
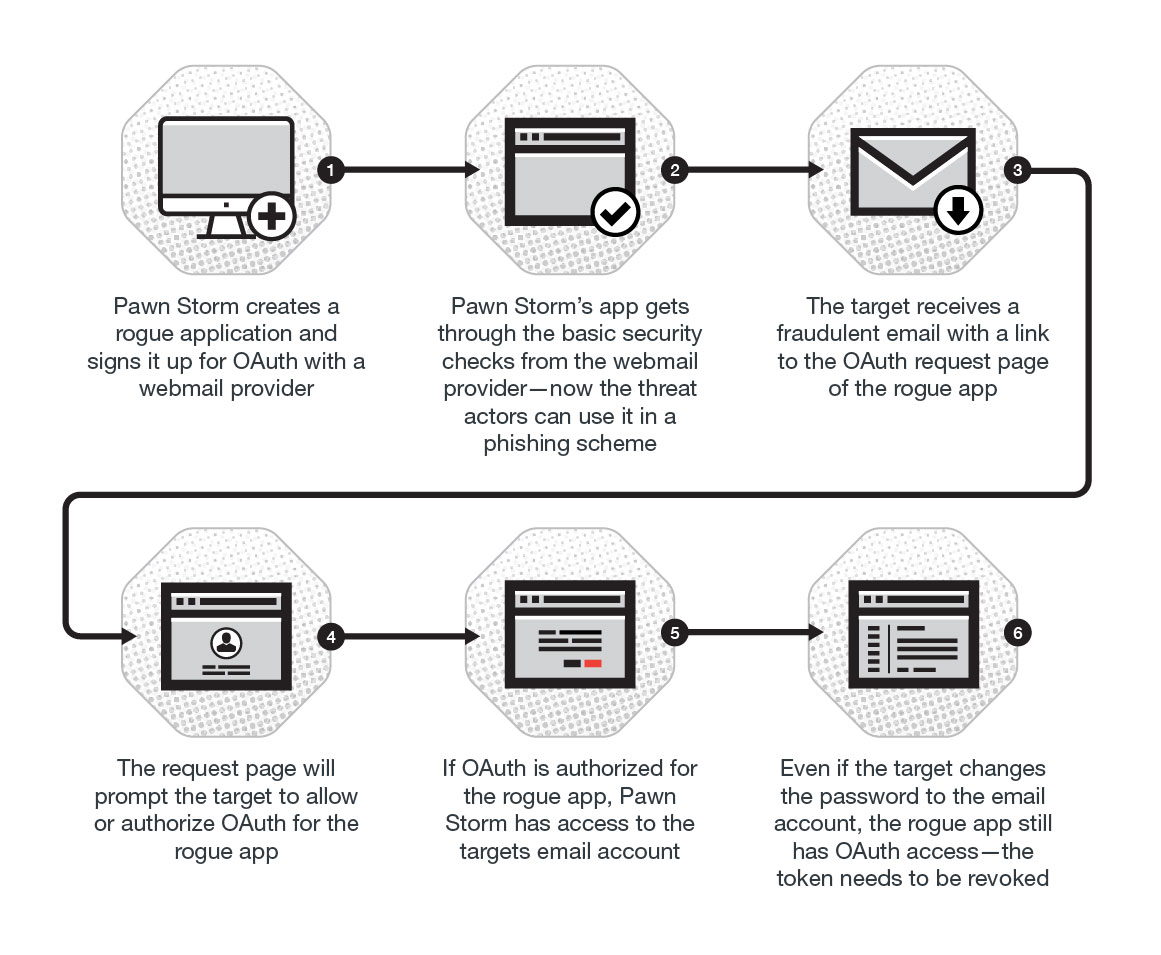
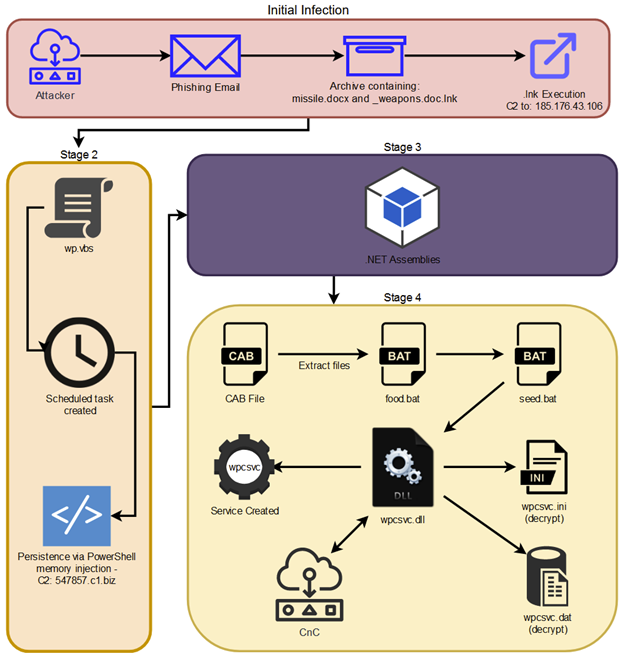
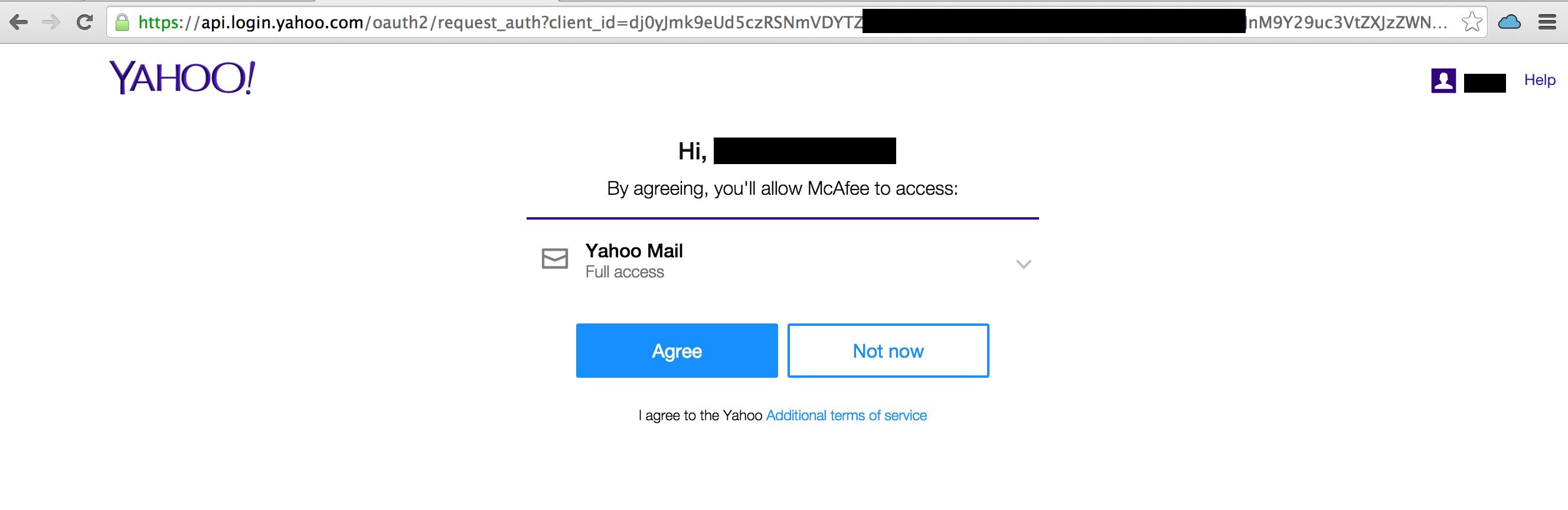
This blog post discusses how Pawn Storm abused Open Authentication (OAuth) in advanced social engineering schemes. High profile users of free webmail were targeted by campaigns between 2015 and 2016.
APT28 Archives - Security Affairs

Pawn Storm Abuses OAuth In Social Engineering Attacks
Pawn Storm's Lack of Sophistication as a Strategy

What is Social Engineering?
GitHub - netskopeoss/phish_oauth: POC code to explore phishing attacks using OAuth 2.0 authorization flows, such as the device authorization grant.

How to Protect Against Social Engineering Attacks?

APT28 relies on PowerPoint Mouseover to deliver Graphite malware
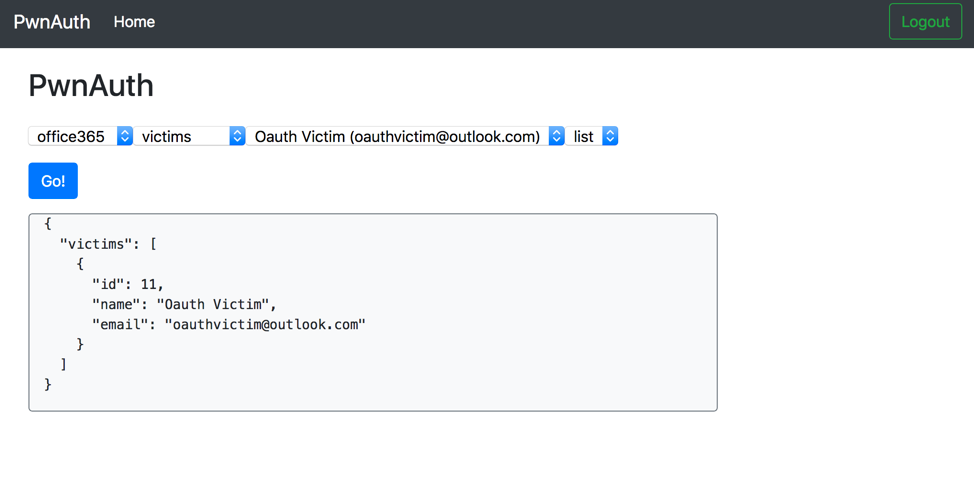
Shining a Light on OAuth Abuse with PwnAuth

What Are Social Engineering Attacks and How to Prevent Them - SEON

Social Engineering Attacks: Definition, Examples, Prevention
Pawn Storm Abuses OAuth In Social Engineering Attacks
DEF CON 29 - TIB AV-Portal
Recomendado para você
você pode gostar