Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 11 novembro 2024
11 Best Malware Analysis Tools and Their Features

Malware Analysis Benefits Incident Response
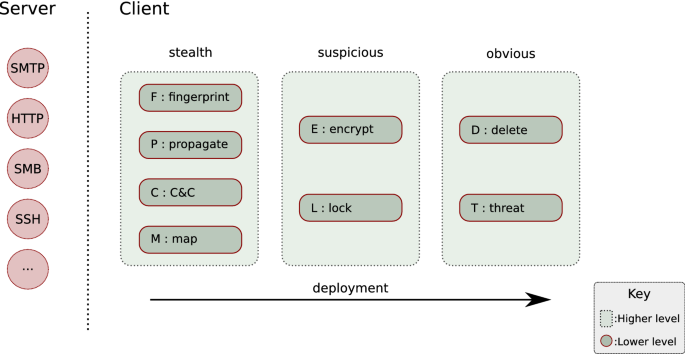
Ransomware deployment methods and analysis: views from a
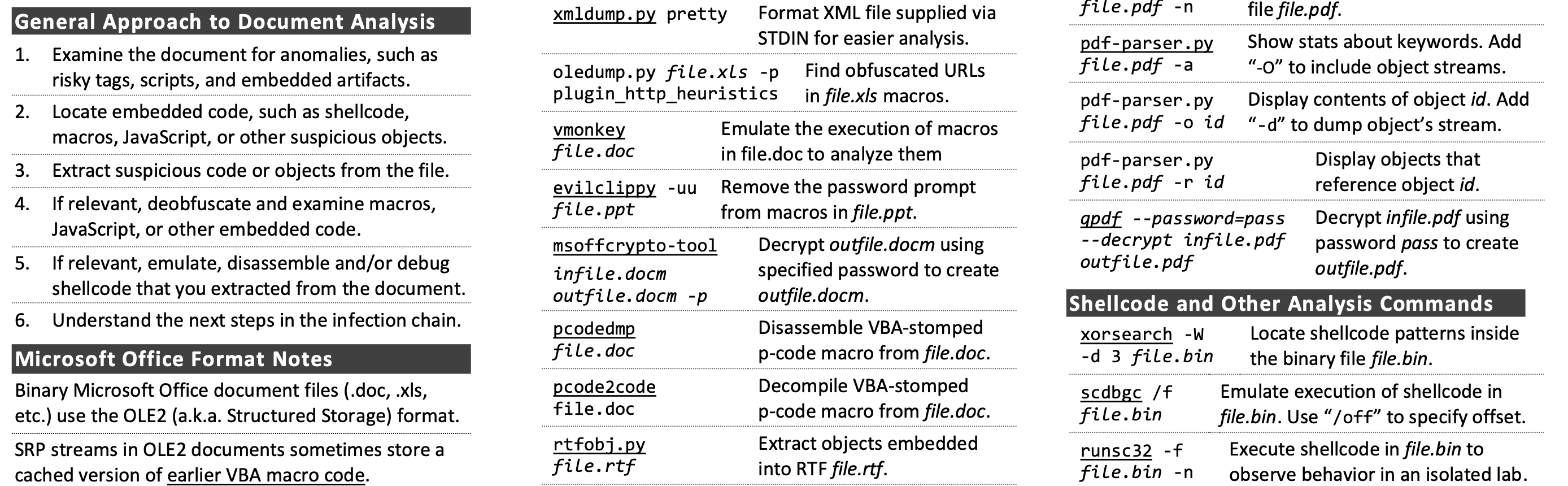
Analyzing Malicious Documents Cheat Sheet
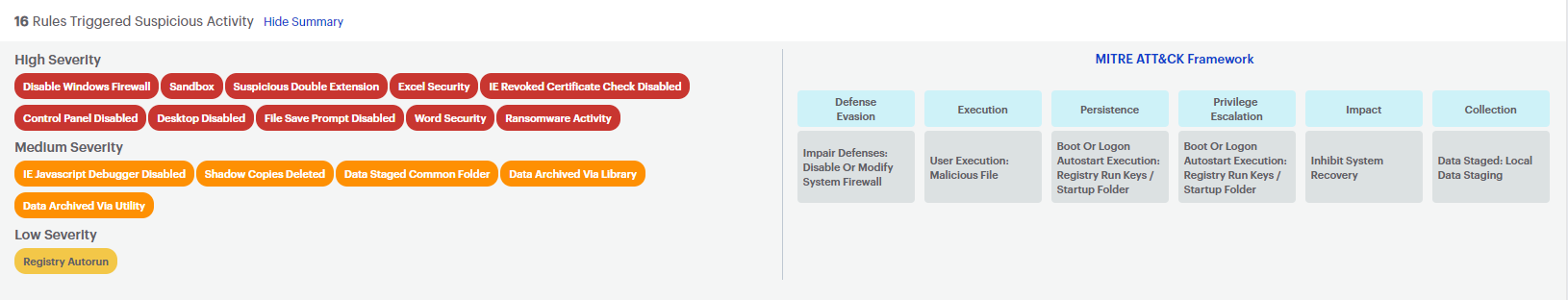
Living Off the Land (LOTL) Attacks: Detect Ransomware Gangs
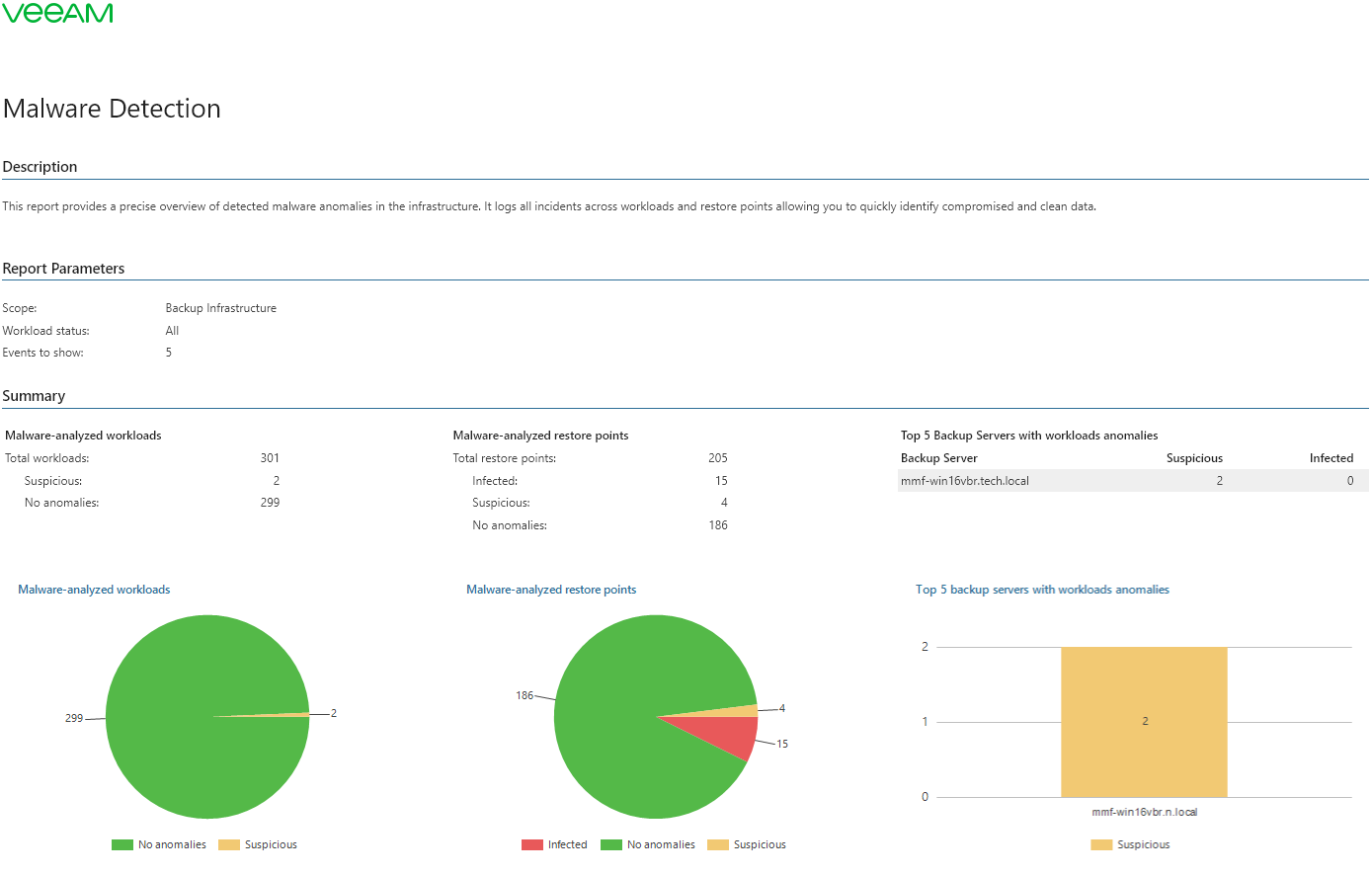
Malware Detection - Veeam ONE Reporting Guide

7 Benefits Of Dynamic Malware Analysis
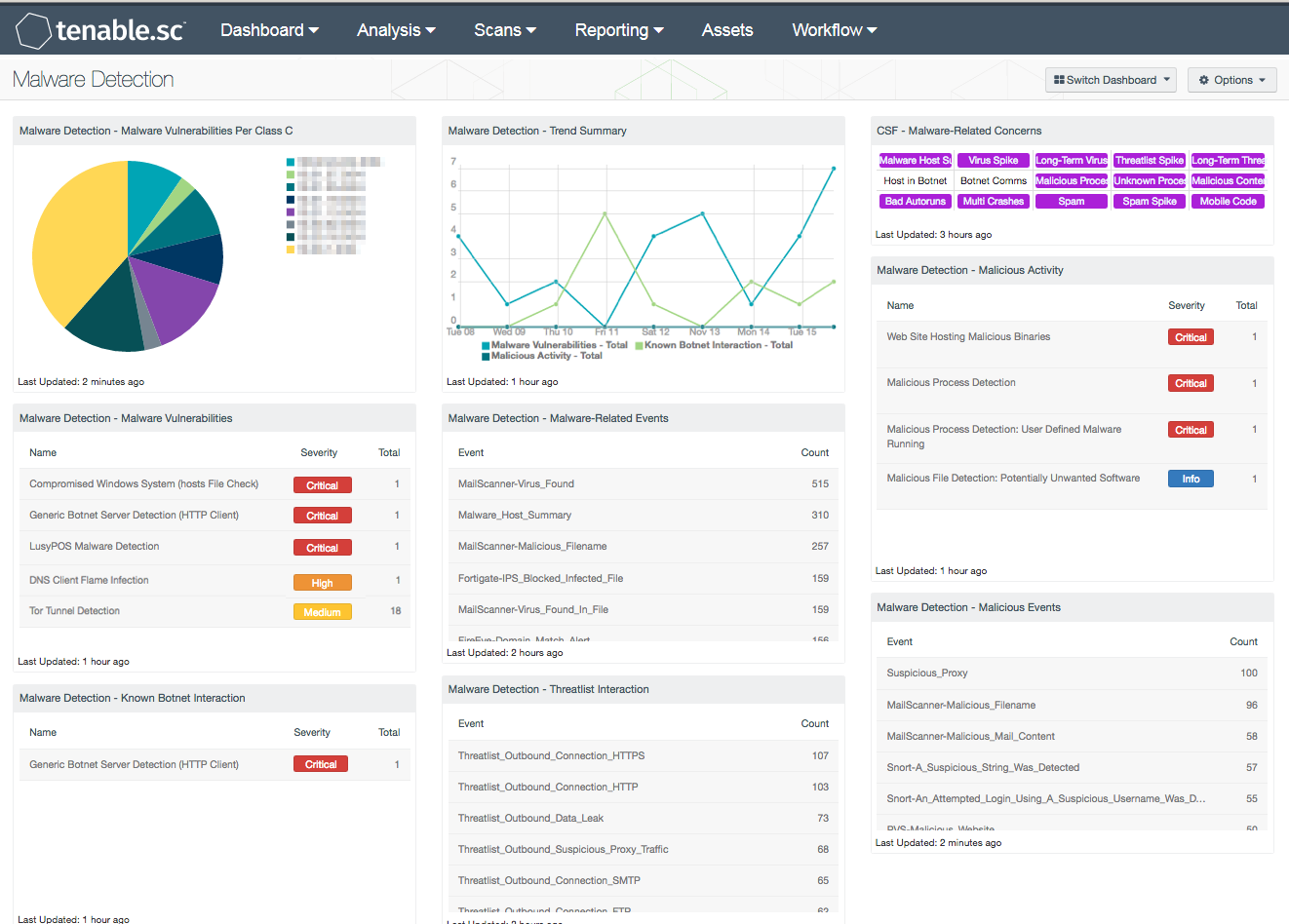
Malware Detection - SC Dashboard
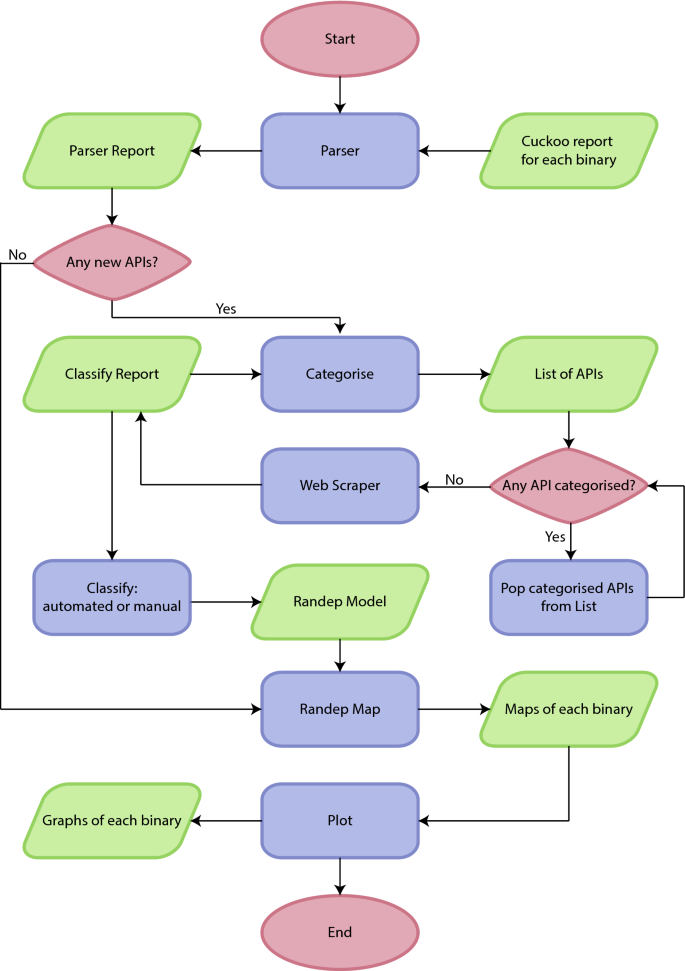
Ransomware deployment methods and analysis: views from a

Malware Detection: 7 Methods and Security Solutions that Use Them
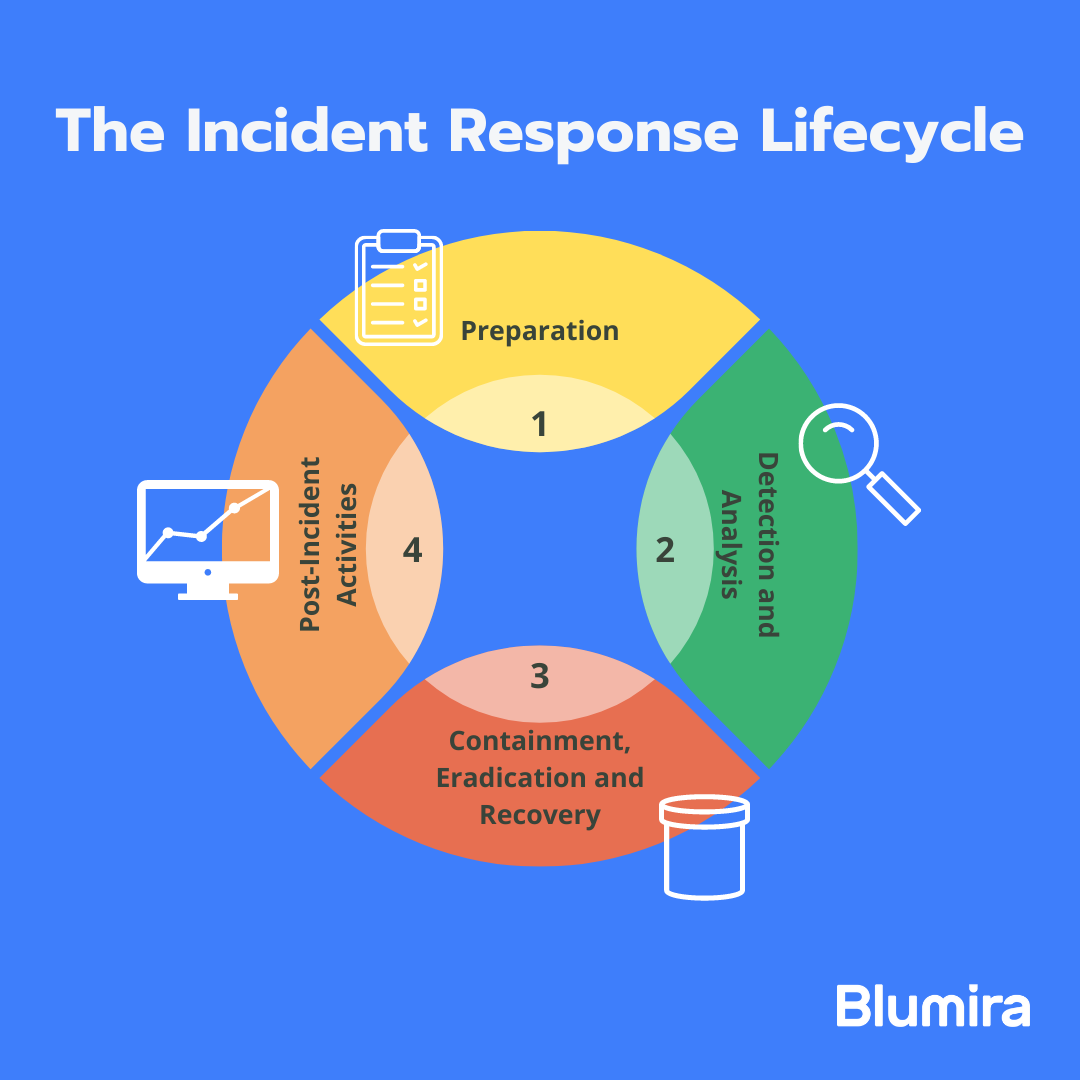
Building Effective Incident Response Procedures
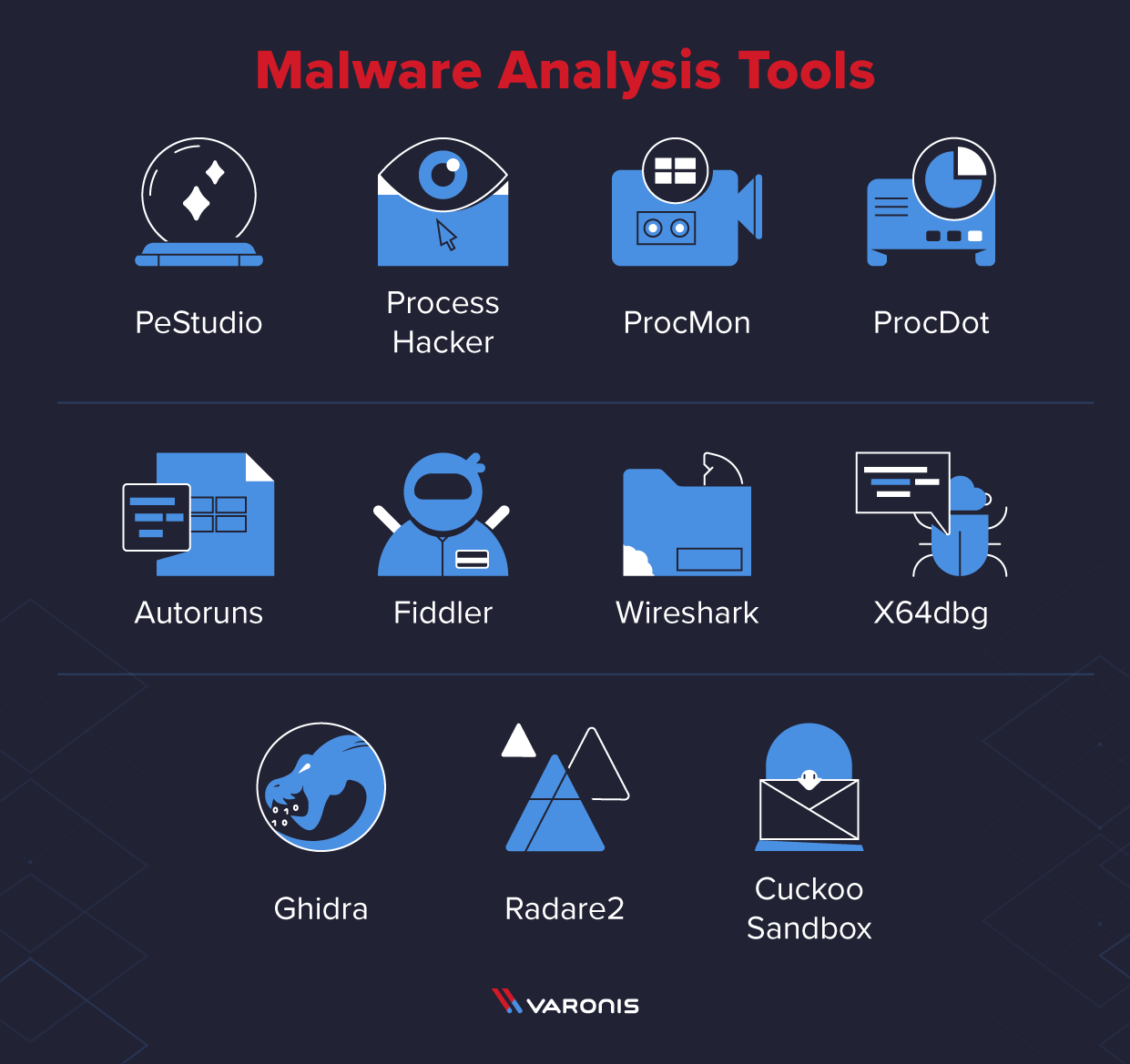
11 Best Malware Analysis Tools and Their Features
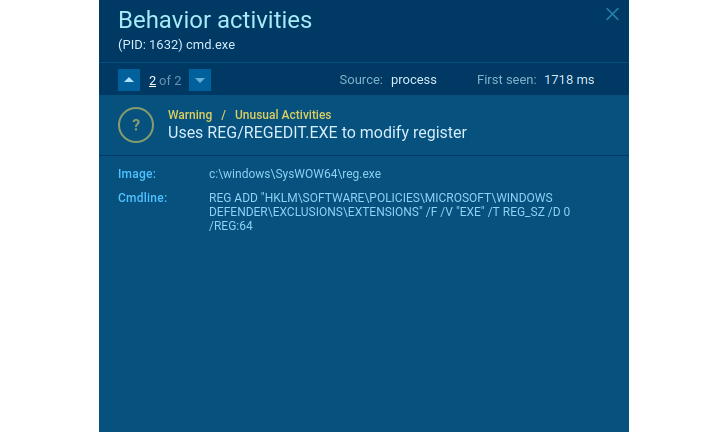
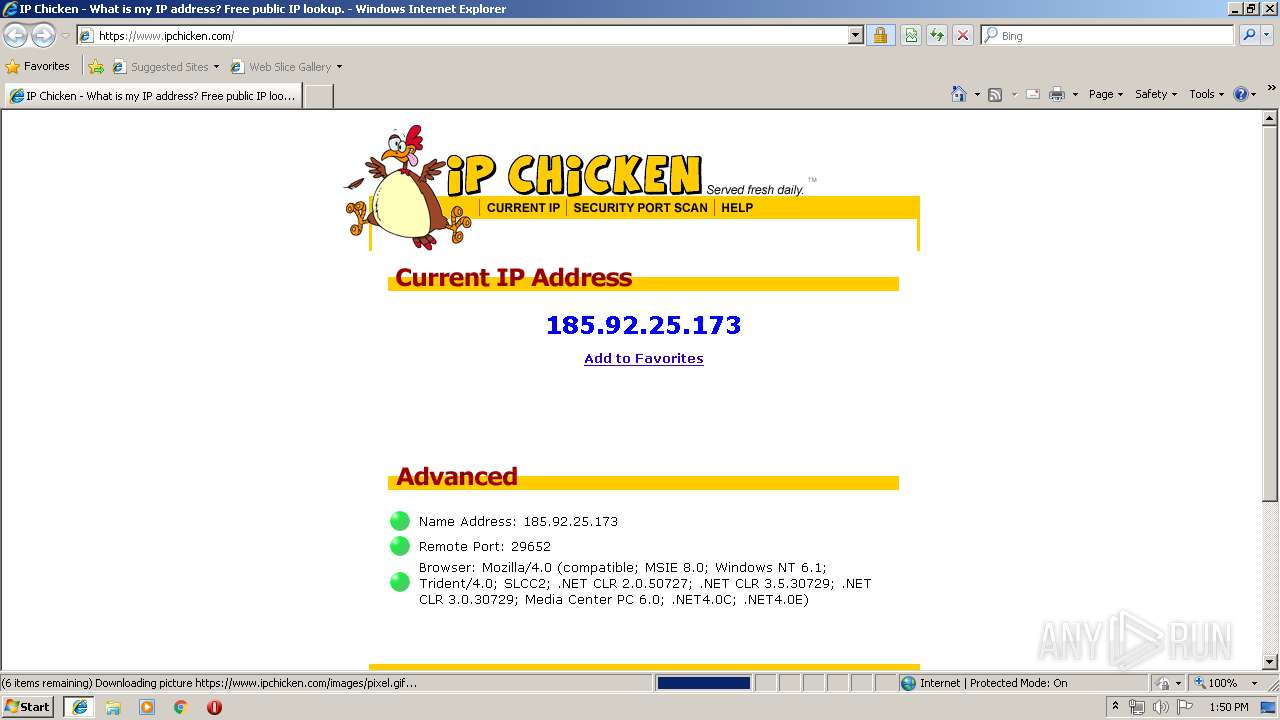
How to Detect New Threats via Suspicious Activities

Behavioral blocking and containment: Transforming optics into
Recomendado para você
você pode gostar