HTB: Investigation
Por um escritor misterioso
Last updated 12 novembro 2024

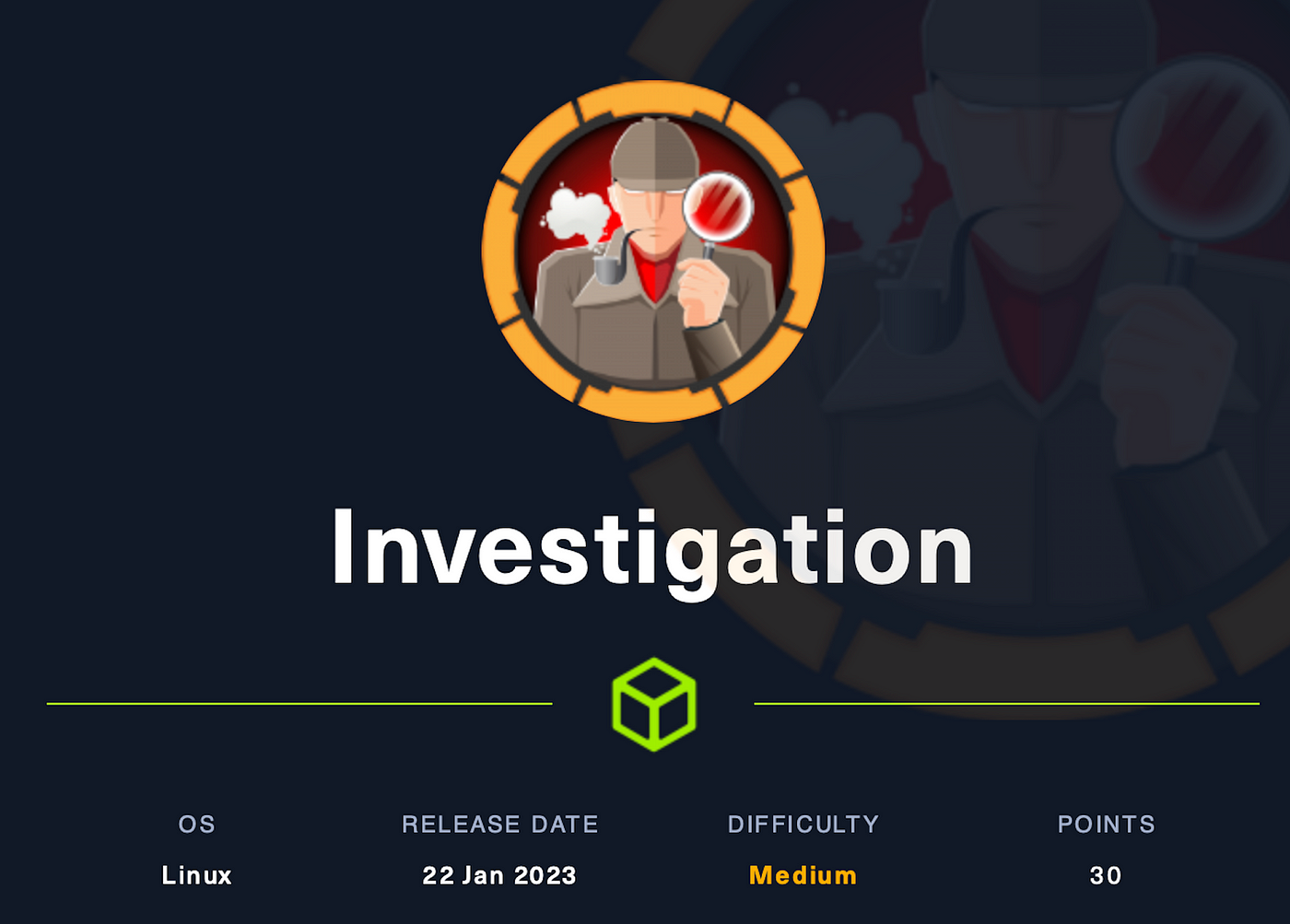
Investigation starts with a website that accepts user uploaded images and runs Exiftool on them. This version has a command injection. I’ll dig into that vulnerability, and then exploit it to get a foothold. Then I find a set of Windows event logs, and analyze them to extract a password. Finally, I find a piece of malware that runs as root and understand it to get execution.

Part 3: How the HTB research was done and what's coming up in the main chapters. – Your name is like honey
HTB — Investigation. A detailed walkthrough for solving…, by Niraj Kharel

INTERPOL on X: Busy week in Lomé 🇹🇬, where 40 Togolese police officers were trained on security document examination & crime scene investigation of terrorist attacks. Building capacity to boost the fight

HTB Investigation. The machine consist of exploiting…, by Damaidec

HackTheBox Bolt walkthrough

PDF) Statistical Investigation of the Disturbances Affecting the Power Distribution Networks (HTB/HTA) of a Few Source Substations in South-Benin

HTB — Investigation. A detailed walkthrough for solving…, by Niraj Kharel

HTB: Investigation

Hack The Box on X: Mirror mirror on the wall, who is HTB CDSA for? 🪞 Check out the job titles this new #defensive certification will prepare you for. Spoiler alert: it's
Hack The Box Machine Write-Up: Keeper [Easy]
Investigation (Medium)

Hack The Box on LinkedIn: #binary #cybersecurity #hacking #htbacademy #hackthebox #htb…
Investigation - HackTheBox Machine
Recomendado para você
você pode gostar