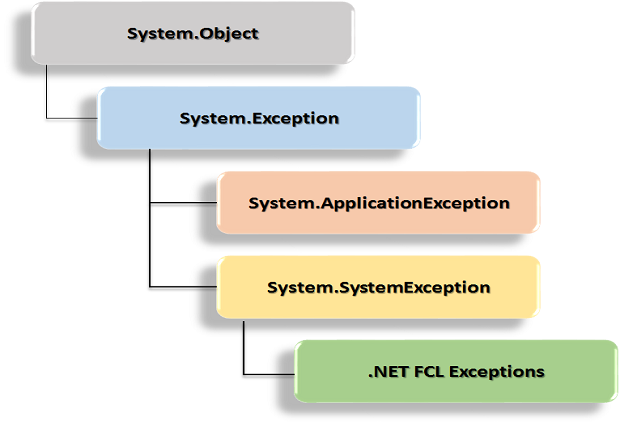
Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Last updated 10 novembro 2024

In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

PowerShell Best Practices for Preventing Abuse - Cyber Gladius

What is an Integer Overflow Attack (with Examples)?
Mitigating Abuse of Android Application Permissions and Special

exception processing message 0xc0000005 - unexpected parameters
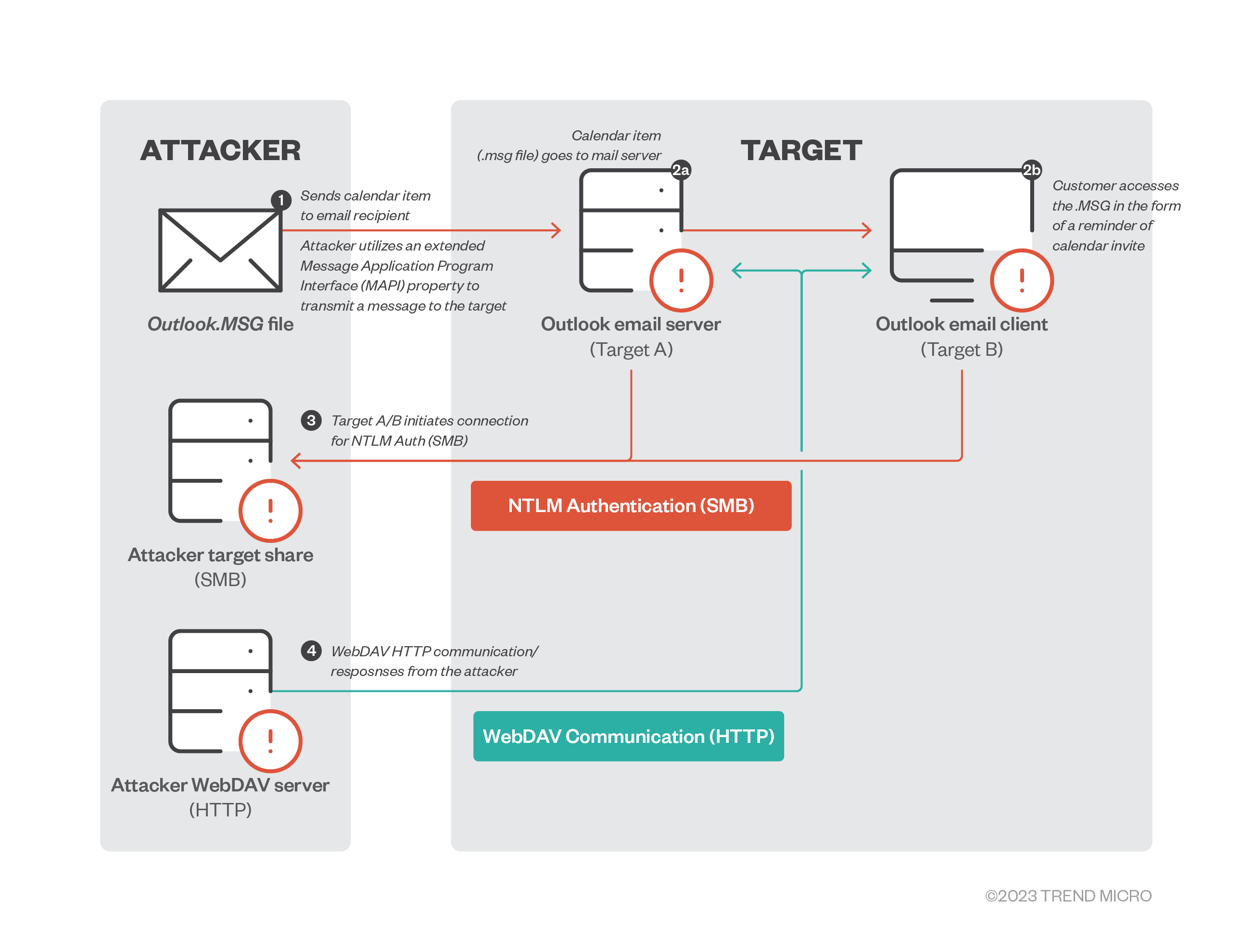
Patch CVE-2023-23397 Immediately: What You Need To Know and Do
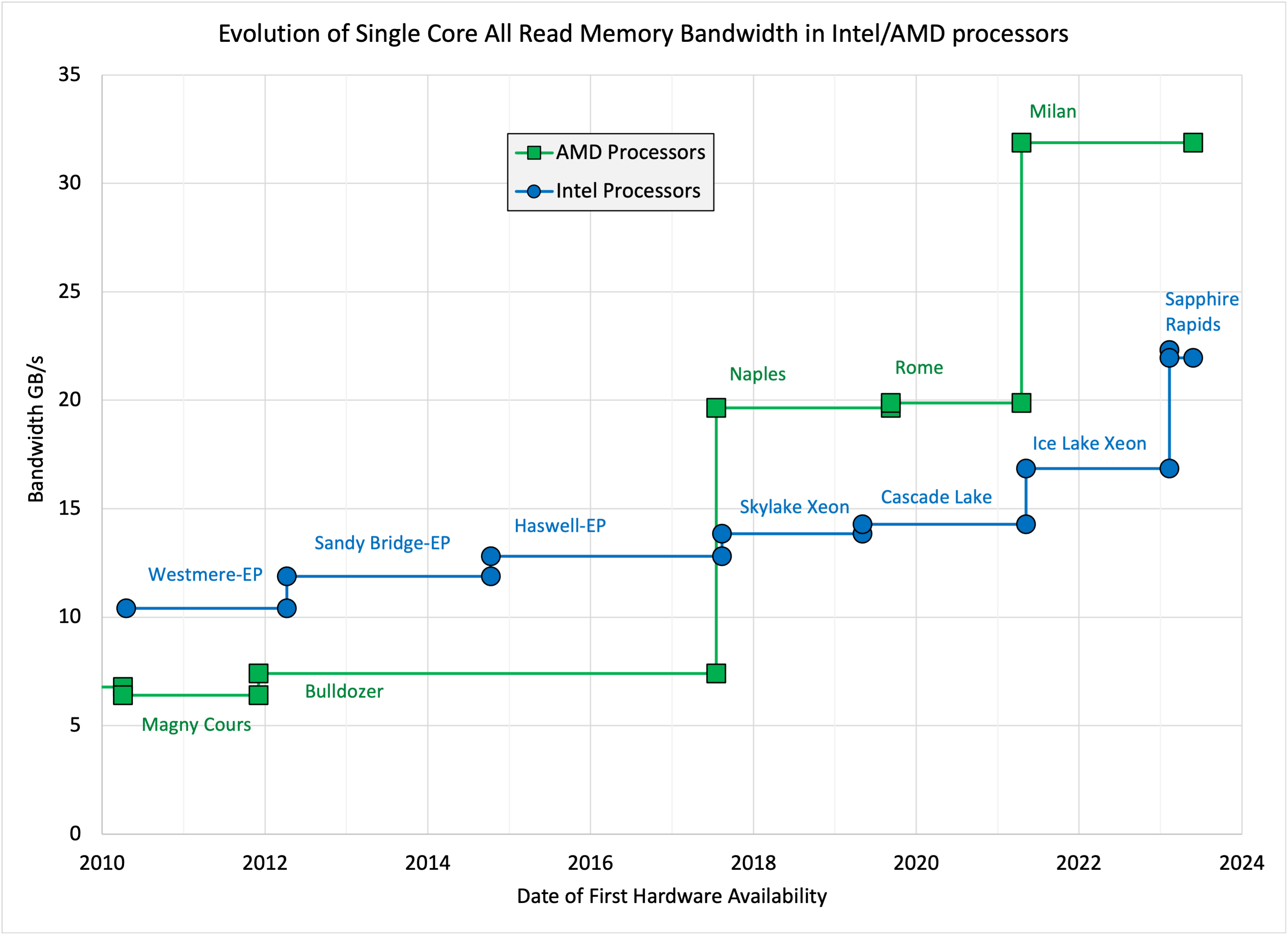
John McCalpin's blog » STREAM benchmark

Abusing Windows Internals - Part Two

Secure Your AWS EC2 IMDS - Tenable Cloud Security
Log4Shell Zero-Day Vulnerability - CVE-2021-44228

Changing Spring Boot Env Properties at Runtime
Recomendado para você
você pode gostar